Recent searches
Search options
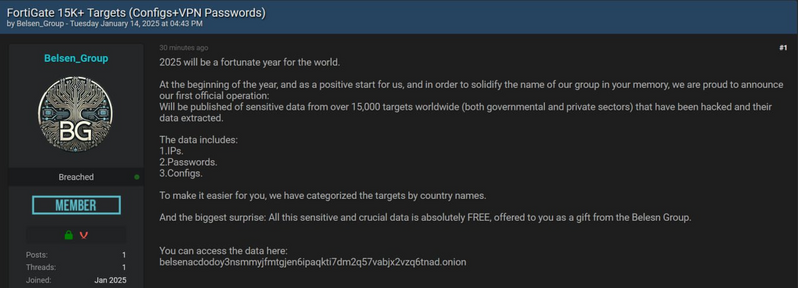
A new group, Belsen Group, claim to have released Fortigate configs for 15k firewalls.
The ZIP contains a folder for each IP address, inside is config.conf (Fortigate full config dump) and vpn-passwords.txt.
The Fortigate config data appears legit - they're unique - and it looks like a very serious cyber incident is going to play out. Some align to Shodan.
All the configs appear to come from Fortigate 7.x devices, so this is probably the latest zero day Fortinet didn't tell people about (edit: update in thread, some are 7.2.x devices).
In terms of validity, you can directly match up devices between the IPs and config.
The VPN usernames and passwords are in plain text. There's also the device certs etc.
A small number of the devices are on Fortigate 7.2, versions from late 2022 - which tends to blow the recent CVE out of the water as that's not supposed to be impacted.
I've confirmed one of the usernames and passwords with one of the victims a friend works at. Impacted orgs are going to need to change local SSL VPN passwords, admin passwords etc.
If anybody wonders if it's related to this prior Fortigate SSL VPN dump: https://www.bleepingcomputer.com/news/security/hackers-leak-passwords-for-500-000-fortinet-vpn-accounts/
I don't think so. The configs run to a year later version wise, and the IP addresses in that dump don't align with this dump.
The other thing to mention is the prior dump was via CVE-2018-13379. These devices, based on the config dumps, are largely running versions which were long ago patched for that.
So what = later vuln.
Off to bed now, plan for later on tomorrow is to publish the impacted IPs so orgs have a chance to know if they're in scope.
The last time somebody did this, it was a ransomware group as basically a freebie to attract operators.
Regarding 'the data's old':
a) the version numbers run up to 2 years ago, that's not very old
b) many of the devices are still online and reachable
c) there's data in the dump which has not been published before as far as I can see, along with device configs
One final update - did some IR on an impacted device, it looks like CVE-2022-40684 based on artefacts left behind.
It also looks like the data was assembled in October 2022 and only just released, looking back at historic IP records vs the dump. So basically if your config might be in the dump even if you patched, as it was a zero day at the time.
Also in the dump is complete firewall rules for the devices.
1.30am bloggo I wrote
Everything I know about the Fortigate config dump situation
Also, Belsen was a exchange camp, where Jewish hostages were held with the intention of exchanging them for German prisoners of war held overseas.
GitHub repo with the FortiGate config dump IPs. If you’re on this list, you need an incident to rotate creds etc.
https://github.com/arsolutioner/fortigate-belsen-leak/blob/main/affected_ips.txt
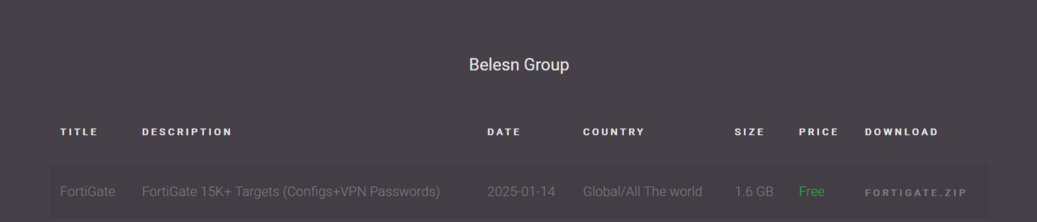
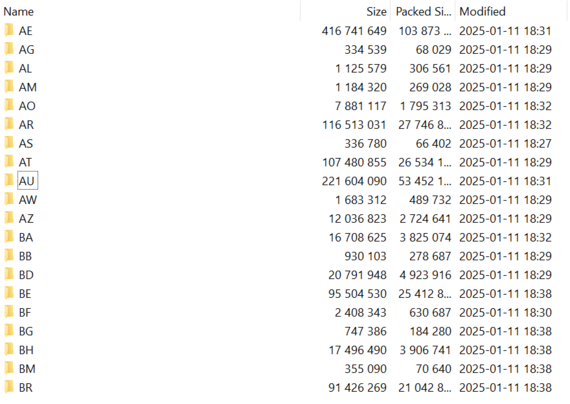
Here's how the data was organised, by country (Australia and UAE love Forti).
The data appears to have been assembled for release starting on the 11th, based on the modified dates (but was collected years earlier).
Plan for later today is release an Excel file with IPs, reverse DNS, ASN org names and numbers, country etc so orgs can better surface their exposure. Will post here and update blog post.
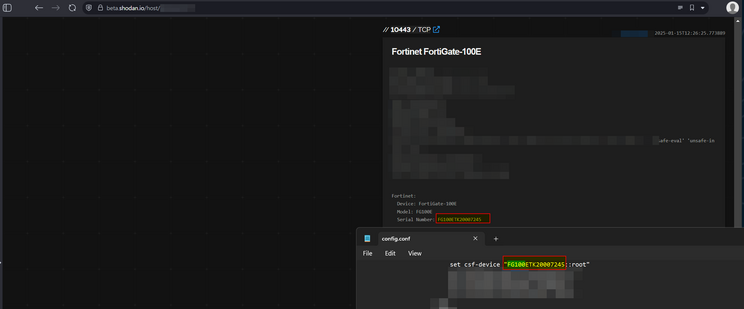
Also, in terms of data validity - I have an automated process scraping HTTP requests for serial numbers and comparing to serial numbers in config files for same IPs: it's legit, they match.
Updated my blog on the Fortigate situation (at the bottom). Nothing particularly interesting.
Also, the blog has pretty significant traffic, just looked at the numbers - but less than 4% from Twitter. That would have been unthinkable a few years ago.
FortiGate have a blog out: https://www.fortinet.com/blog/psirt-blogs/analysis-of-threat-actor-data-posting
It’s essentially the same as my blog - but in corporate
It plays heavily on the ‘this is old data’ angle and says you’ll be fine as long as you rotated credentials. Sure, somebody obtained all your firewall rules.. but that’s okay.. right.
To help defenders find their impacted orgs in the Fortigate configuration dump incident, here's all emails mentioned - Ctrl+F for yourself.
Obvious point - not everybody puts their email address in a config file.
Also, one of the things I've seen mentioned about this dump (including by Fortigate, bizarrely) is 'old IPs, none of these are live'.
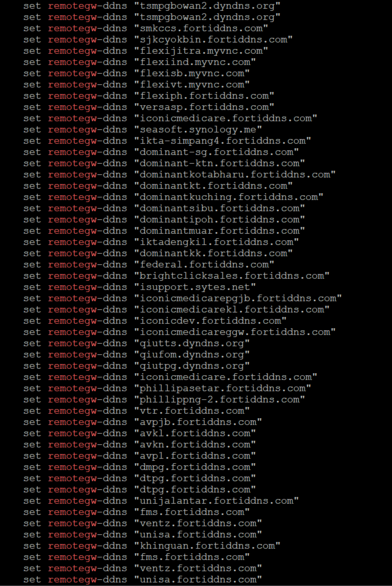
Tip: remotegw-ddns feature. Fortinet even offer dynamic DNS as a service so the IPs float by design. A lot of them are hanging off that.
One other side effect of the FortiGate config incident is there’s several thousand site to site IPsec VPN configs allowing you to straight up join to the internal network of large orgs.
So even if you weren’t popped, the threat actor can pop up on your network.
If anybody is wondering:
$ cat */*/* | grep -c "ike-version"
11917
11.9k IPsec VPN tunnels (some orgs have lots).
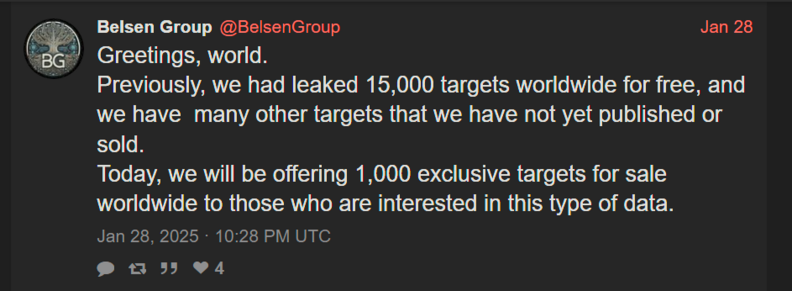
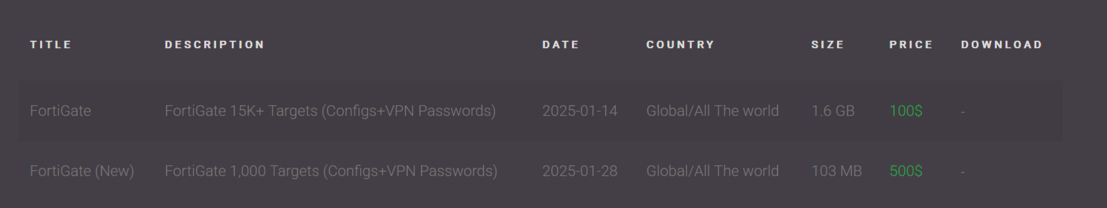
Belsen Group are back and can spell their own group name now. #threatintel
This is what they're trying to sell, they're also trying to sell the original dump for some reason.
They don't appear to have a way to actually sell the data as the links don't point anywhere, which is a slight flaw.
@GossiTheDog Gotta feel a little sorry for the poor bud who's gonna have one hell of a rude awakening tomorrow when he see's a bunch of devices he recognizes as the ones he thought they'd already patched... 2025 is going to be one bumpy ride.
They need to get their management interface off the Internet or they'll be back here again and again.
Thanks for all of this, as ever. Wondering if anyone pulled all of this down and re-uploaded the full dataset anywhere as the original appears to be down?
@GossiTheDog any devices belonging to Maldives?
@GossiTheDog I read half a VPN password aloud to a victim on the phone, they completed the other half. They're *definitely* legit. They also seem to be mostly cleartext, even those not looking like cleartext?
@GossiTheDog appreciate getting the IP dump link in thete, was able to highlight it to one affected org I have contacts with.
@GossiTheDog oh that’s ok, everyone’s got approximately the same firewall rules anyway
@GossiTheDog also running FortiOS 7.6 or 7.4 in 2022 wasn't really a good idea for the stability of your network.
@GossiTheDog
> If your organization has consistently adhered to routine best practices in regularly refreshing security credentials and taken the recommended actions in the preceding years, the risk of the organization’s current config or credential detail in the threat actor’s disclosure is small.
So, basically: please rotate all your firewall credentials daily considering that 0days are released basically every day on our products at the moment.
That's top advice
@GossiTheDog Phew, our company is not there. Thank fuck for that.
@GossiTheDog none of these are live? How fast does forti think their hardware gets rotated out, exactly?
@GossiTheDog lotta .gov addresses in there.
@GossiTheDog I would imagine plenty of folks use DDNS because it's easier and cheaper than a dedicated IP, especially for services where you're not really concerned with having a "pretty" vanity domain name.
@GossiTheDog yet another win for denying client and vendor IPsec tunnels everyone forgets exists
@GossiTheDog and fortigate has some interesting bugs and quirks with how they handle ike/ipsec traffic. The firewall local-in handler, for example, does zilch for esp packets.
@GossiTheDog I see Belsen Group is now ... charging for the leak? I suppose to capitalize on demand. :/
I know some copies are floating around from before the $100 price was added - I have a copy and have a mirror/torrent ready. Before yeeting it into the world I did want to quickly check: I haven't looked at the details of this in the same depth you have, so if it's best to limit copies floating around right now I'm happy to hold off on publishing my mirror.
Edit: I ain't the first, so yeet
@GossiTheDog there is a malware in his github (AKboss1221 Fortigate Belsen Leak} be careful from {Lua.exe}
@GossiTheDog It would be nice if Fortinet supported more general 2FA solutions vs. their paid fortitoken system.
@GossiTheDog
To just see the list of domains, try this abuse of commands:
wget -qO- 'https://github.com/GossiTheDog/Monitoring/raw/refs/heads/main/Fortigate-Config-Dump-emails.txt' | grep 'set email-to' | cut -d ' ' -f 11 | cut -d '@' -f 2 | cut -d '"' -f 1 | sort -fu
(Hopefully that formatted well.)
@GossiTheDog what's the HTTP call to get a fortinet to return it's serial number? I thought that required authentication
@GossiTheDog this is yeoman's work; thanks for putting in the effort
@GossiTheDog I just downloaded the list of IPs and was planning on running my geolocation script on them but need to remove the port first (or to update my script to ignore it).
@GossiTheDog json instead of xlsx & no country code but: Already includes the IP->AS#, AS Name & reverse DNS(ish) mapping: https://gitlab.com/-/snippets/4795884
@GossiTheDog Thanks for sharing this.
We just checked for our IP ranges (nothing in there) but one of my colleagues grouped the IPs in the repo by AS - funnily enough, a good number of the top few are AS from which we frequently see DDOS traffic against our services. Perhaps suggests a lack of care & maintenance on their part & that the DDOS are likely from/via compromised kit. Not a major surprise.
@tdp_org @GossiTheDog I find the absence of, e.g., 3320 in that list a bit odd.
@GossiTheDog A quick look suggests there's a lot of dynamic IPs in there. few static entries as well.
However an org might still recognise its host ISP as a way of identifying itself.
sed -i 's/\(^[0-9.]*\)\(:.*$\)/-x \1 +noall +answer +authority/' affected_ips.txt
then
dig -f affected_ips.txt >> forti-domains.txt
then just grep for your ISP.
Although if you _think_ youre on the list, maybe just roll creds anyway
@GossiTheDog Thanks for the github list. Company network blocks Tor ;)
@GossiTheDog Thank you for sharing this
@GossiTheDog can you share a zip file out of onion?
@emme @GossiTheDog
that would be great - am also running a few forti boxes in austria and the provider ip might have changed so it would be hard to verify only on this information
@elementalsitservices @emme @GossiTheDog
Kudos to Amran Englander - he published the full IP list here to verify if you're on it : https://github.com/arsolutioner/fortigate-belsen-leak/blob/main/affected_ips.txt
@saanv @elementalsitservices @GossiTheDog great but I need configuration too
They apparently took down the TOR site a few hours ago. I was trying to download so we could do notifications to entities affected in our AOR.
Same for me :(