Recent searches
Search options
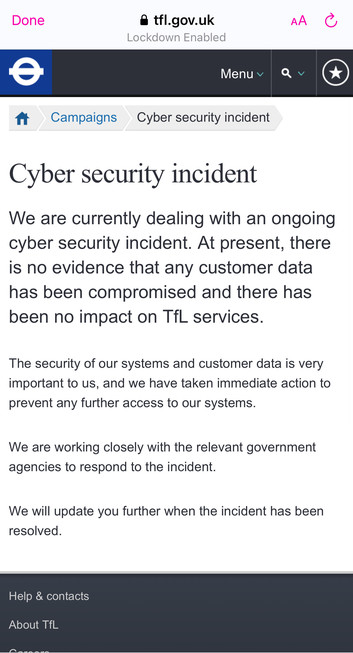
Apparently Transport for London are dealing with a cyber security incident.
It’s buried on their website, not on the front page or news sections, and has no date on it. https://tfl.gov.uk/campaign/cyber-security-incident
HT @joshbal4
Orgs, you probably don’t want to email a million people at 6.30pm saying ‘whoopsie we have a happy little cyber incident’ with no actionable info as it will just spark concern and leave an information void for people to fill themselves.
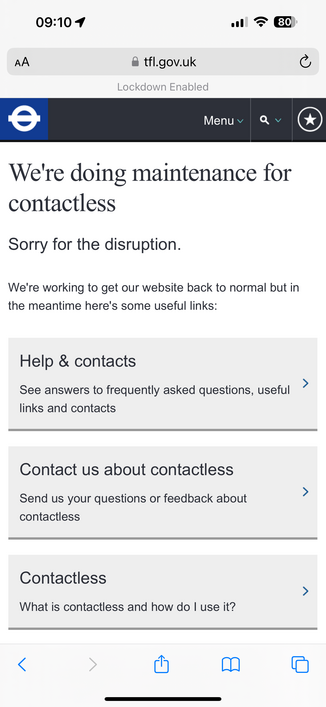
Transport for London has set the contactless sign in link to Maintenance mode.
Transport for London have a genuine internal security incident running and are reverting to paper processes. #threatintel
Transport for London have shut down outbound internet access and restricted systems inbound, eg they have cut off some Netscaler VPNs but left up others for home users.
They appear to be doing a containment. Unclear if ransomware so far as haven’t had time to crawl network traffic.. but it’s the containment steps you take for ransomware and extortion groups.
Looked into this, the TfL API server for tube data is down (has been for about a day)
The Transport for London cyber incident is still ongoing.
The attackers got onto the corporate network, which is currently contained for recovery.
The operational (ICS) network wasn’t reached so services to customers continue uninterrupted.
Boundary internet services often offline, VPN restricted to home users, ERP systems, API systems etc offline.
If anybody is interested, the Transport for London cyber incident is still ongoing 3 days later - systems remain contained.
Two of the systems shut down https://beta.shodan.io/host/195.40.85.10
If anybody is wondering, Transport for London are still in containment 5 days in.
APIs, ERP etc still offline.
Update on Transport for London incident.
I can see prior traffic from their network to a crimeware group. #tfl #threatintel
Transport for London are still in containment phase, 7 days into their cyber incident.
Hopefully it focuses minds on boards who believe large scale cyber incidents can be resolved in a day. #tfl #threatintel
Day 9 of the Transport for London cyber incident
Two updates
- I’ve confirmed they’re still in containment phase, and internal services and API remain down.
- @zackwhittaker has an excellent spot - they’ve removed the statement about no evidence of customer data exfiltration, and then not commented when asked about it. https://techcrunch.com/2024/09/10/londons-transit-agency-drops-claim-it-has-no-evidence-of-customer-data-theft-after-hack/
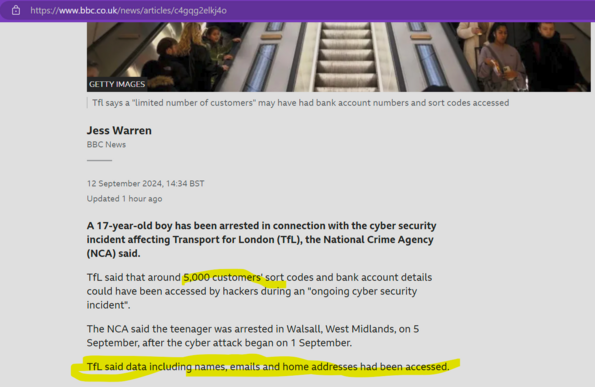
Transport for London tell me they have identified data exfiltration of customer names, contact details, email addresses, and - in a small number of cases - bank account numbers and sort codes.
They are still in containment phase. #tfl #threatintel
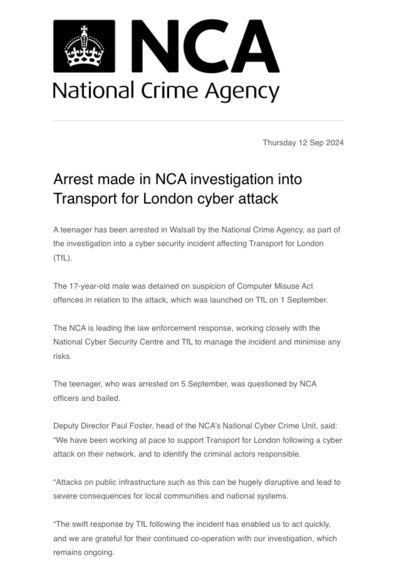
The NCA have arrested a teenager over the Transport for London hack HT @mattburgess #tfl #threatintel
For any press covering the #TfL hack - the 5000 bank accounts is separate to the customer names, emails and home addresses bit.
TfL didn't say how many people's details overall were accessed.
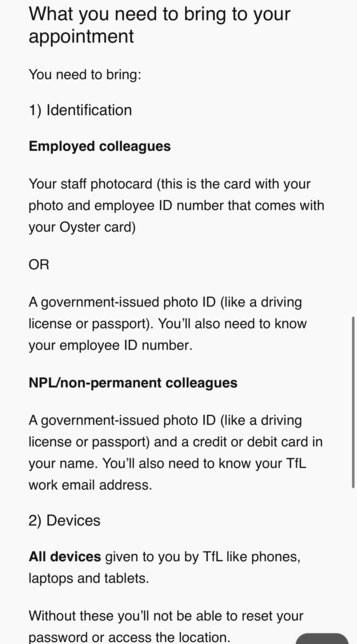
One of the things TfL have done in their containment phase is locked their IT staff's accounts, who aren't working on recovery -- and they're working to manually reauthenticate who their staff are, i.e. check their identities.
In entirely unrelated () news, teenagers in LAPSUS$ and Scattered Spider often obtain access by calling up the helpdesk and saying they've lost their phone for MFA and/or forgot their password. Your containment playbooks should include stripping MFA devices.
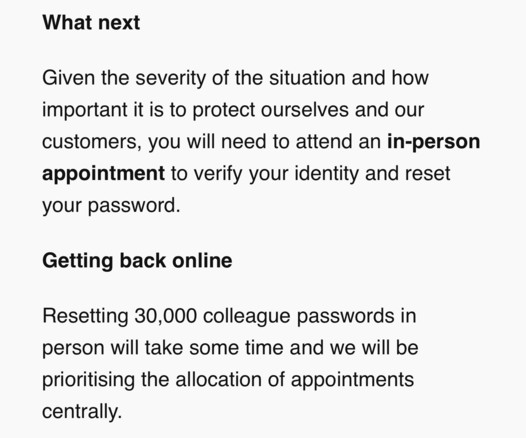
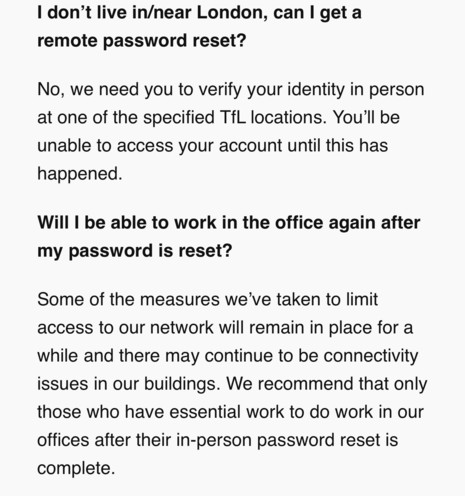
Transport for London latest - they are resetting the login and MFA details for 30,000 employees in person, accounts are locked. #TfL #threatintel
The #TfL queue to get account access back is out the buildings and down the roads #threatintel
FWIW I’ve heard the TfL incident is Scattered Spider again, in a surprise to nobody - ie teens phoning helpdesks to gain access. #TfL #threatintel
Btw, I think Transport for London have done a really good job containing this. It would have been much worse, one suspects, had they not.
It sucks for staff but they prioritised customer service (i.e. transport) and safety over short term recovery, and that is very likely the correct pivot. I've seen these things go the opposite direct when orgs under react and it often ends really poorly.
Message from head of Transport for London to staff about their cyber incident, sent out to staff via WhatsApp. #tfl #threatintel
Transport for London on if this was a ransomware or extortion group: “It is not appropriate to comment on this while the investigation is ongoing.”
Transport for London say they have completed containment stage of their cyber incident and are on their way through recovery. #tfl #threatintel
@GossiTheDog what exactly does that mean - who is in control of their infrastructure? and does that mean that the attack is still ongoing?
@GossiTheDog plus side. Trains still running.
@Jplonie @GossiTheDog They have their priorities straight
@GossiTheDog oof. that's rough. hope they get out of containment and back into regular service soon.
@GossiTheDog do they have to eventually reported publicly what is happening?
@GossiTheDog #alt4you #london #LondonTube
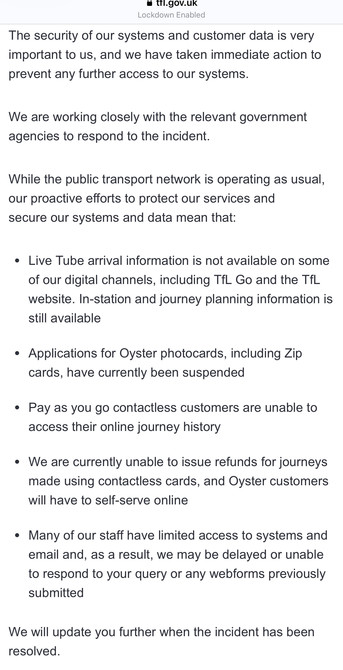
The security of our systems and customer data is very important to us, and we have taken immediate action to prevent any further access to our systems. We are working closely with the relevant government agencies to respond to the incident. While the public transport network is operating as usual, our proactive efforts to protect our services and secure our systems and data mean that: (1/3)
• Live Tube arrival information is not available on some of our digital channels, including TfL Go and the TfL website. In-station and journey planning information is still available
• Applications for Oyster photocards, including Zip cards, have currently been suspended
• Pay as you go contactless customers are unable to access their online journey history… (2/3)
• We are currently unable to issue refunds for journeys made using contactless cards, and Oyster customers will have to self-serve online
• Many of our staff have limited access to systems and email and, as a result, we may be delayed or unable to respond to your query or any webforms previously submitted We will update you further when the incident has been resolved. (3/3)
@GossiTheDog Do we see m/any lessons learned in resilience strategies from any of these incidents?
@secureisd @GossiTheDog hopefully internally to the org they do, but I feel it is unlikely they will publish the results apart from a vague worded "we take our customers privacy seriously" type statements
@GossiTheDog @stufromoz the average is 4-6 weeks from memory.
@GossiTheDog @mattburgess the threat actor APT 71 dubbed Pubescent-Swift
@GossiTheDog ... and having established and tested methods of revalidating users' identity. This isn't something you want to be developing on the fly during an incident.
@GossiTheDog am I reading the last bit right.. That they are not allowing people to work from tfl offices (but presumably able to wfh)?
Seems the opposite of what I expected.
@GossiTheDog I don't get the "non-permanent employees...must bring in a credit/debit cars" bit. What does that prove? Asking them to bring proof of a recent payment from TFL/affiliates (payslip) would be better. And isn't the hardware they are bringing on to be authorised asset tagged which would count as some sort of proof?
@GossiTheDog Time for some "fun" social engineering on the folk in the queue....
@GossiTheDog you don’t need explosives to cripple the transport system.
I wonder if the person arrested has indicated that staff accounts have been compromised, or exfiltrated en-mass?
@GossiTheDog I’m coincidentally in London this week and while I’m sure the IT staff are having the worst week they can remember I haven’t seen a single notice of tube closure anywhere, or even heard a person outside of infosec circles mention it.
@mhoye yeah, they basically totalled their usual IT setup to get the threat actor out and keep (transport) service running. Literally locked 30k accounts and shut down internet, 13 days ago.
@GossiTheDog If you can manage it, this is The Way. Fail over to literally anywhere as long as it keeps service moving, clean as you go.
@GossiTheDog Compare to Colonial Pipeline where they did more damage to themselves and their clients than the initial attack.
@GossiTheDog I wonder if this is because it’s government body. Fundamentally their number one priority would be to keep transport going.
No shareholders that need the number to keep going up.
So they rightfully chose the path that offered the best outcome for their core service offering and kept transport going.
@GossiTheDog do you have a credible link to information about hat your post is about.
@GossiTheDog is it just me or is there no sound?
@meatlotion @GossiTheDog it’s an animated GIF, which cannot have audio
@GossiTheDog: Sounds like an invitation for a phishing campaign.
@GossiTheDog As soon as I heard that a teenager from Walsall has been arrested for this, I started the countdown to the attack being described as "sophisticated"
@GossiTheDog not too quickly though, I got caught on a box junction a few days ago...
@GossiTheDog 45 days and still recovering. Don't always realise it is that long
@GossiTheDog You've already ruled out mass incompetence?
@GossiTheDog good that they chose this route! The only sane way to go
@GossiTheDog @mattburgess Advanced Persistent Teenager
@GossiTheDog @mattburgess i look forward to the interview with this kid on darknet diaries in a few years time.
@GossiTheDog in 2018 I was called in to resolve a major network incident for a medium sized hospital. It took two weeks from when their problem occurred to when I completed the work by fully restoring redundancy, completing the upgrade that had caused the original failure and sorted the hardware/part swaps.
And that was just some misbehaving Cisco kit. Cleaning out the place after a breach? They'll have follow-up for months, at *least*!
Organizationally they'll be responding for years.
@GossiTheDog of course we are interested!! :)