Recent searches
Search options
Very big cyber incident playing out at Snowflake, who describe themselves as “AI Data Cloud”. They have a free trial where anybody can sign up and upload data… and they have.
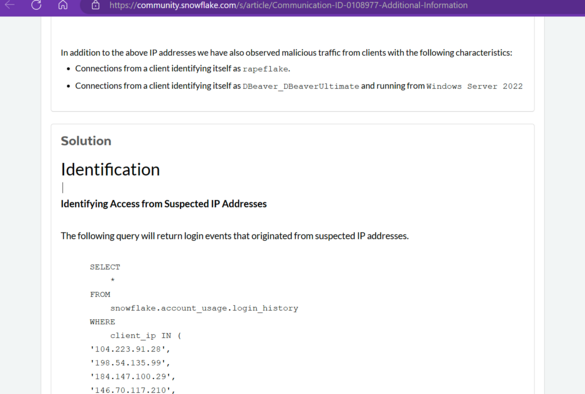
Threat actors have been scraping customer data using a tool called rapeflake, for about a month.
The tl;dr of the Snowflake thing is mass scraping has been happening, but nobody noticed.. and they're pointing at customers for having poor credentials. It appears a lot of data has gone walkies from a bunch of orgs.
Snowflake is a big AI data company with a conference in the US next week, chances of that going ahead are interesting.
IOCs: https://community.snowflake.com/s/article/Communication-ID-0108977-Additional-Information
Snowflake admin users need to check their Snowflake environment, not sec departments check their on prem.
Five orgs have told me they are running incidents for Snowflake, where their data has been copied.
Snowflake: there is absolutely no cybersecurity incident.
Also Snowflake: Please run these commands and look for "threat activity" logins with the user agent "rapeflake" using this knowledge base article we haven't listed on our website.
https://community.snowflake.com/s/article/Communication-ID-0108977-Additional-Information
Live Nation said its stolen database was hosted on Snowflake, a cloud storage and analytics company.
I've now confirmed 6 major orgs running Snowflake cyber incidents, so I've made a theme song about Snowflake's response.
The deleted Hudson Rock post on Snowflake breach: https://web.archive.org/web/20240531140540/https://hudsonrock.com/blog/snowflake-massive-breach-access-through-infostealer-infection
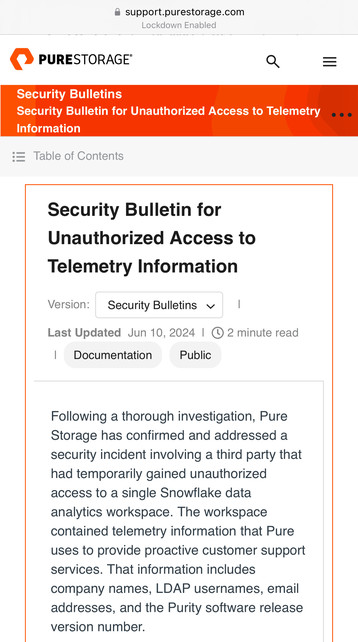
For the record I don't think all the content is accurate - however Snowflake did have a security incident via their former employee, they have full IR stood up. They didn't follow their own best practices.
I also know multiple orgs who've had their full databases taken from Snowflake.
I wrote a blog on everything I know about the Snowflake situation https://doublepulsar.com/snowflake-at-central-of-worlds-largest-data-breach-939fc400912e
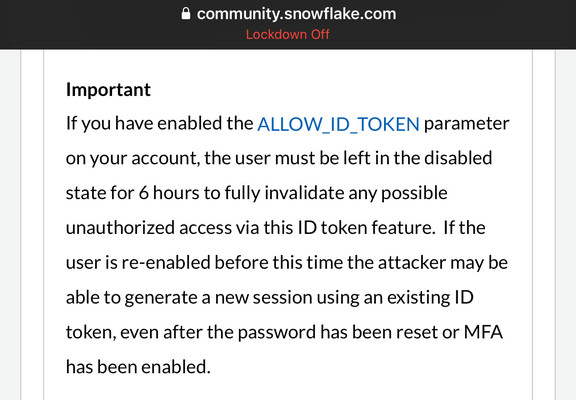
The Snowflake authentication setup is terrible.
MFA can’t be enabled org wide, each user has to manually log in and enable it. There’s no policy to block users without MFA. And it uses Duo MFA rather than your orgs MFA. (You can bring your own MFA with SAML).
Also all users log in via a Snowflake domain, so you can just pull creds from info stealer marketplaces or logs.
That’s why they’re being targeted as a platform.
Hudson Rock have put out a statement saying a legal threat from Snowflake caused them to remove their blog. https://www.linkedin.com/posts/hudson-rock_activity-7203433945919578113-RH05 HT @mattburgess
Another Snowflake customer breach: https://techcrunch.com/2024/06/07/snowflake-ticketmaster-lendingtree-customer-data-breach/
One thing I didn't know until recently is Snowflake has a massive fanbase, Apple and Amiga style - if you critique Snowflake in any way people flip tables. The comments on my blog are fun. I mean, the clue is in the product name, really.
IMHO it's fair to call out Snowflake's authentication isn't very good - it's the worst SaaS MFA solution I've seen as it has no top level, easy switch for org wide MFA enforcement.
Combined with putting all customers under *.snowflakecomputing.com sub domain is why their customers are getting owned - infostealers are just full of creds ready to go.
I gather Snowflake are discussing changes to fix, don't tell the fanboys (and yes, they're all dudes).
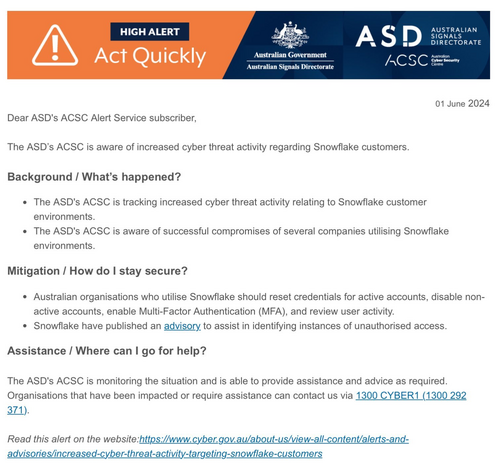
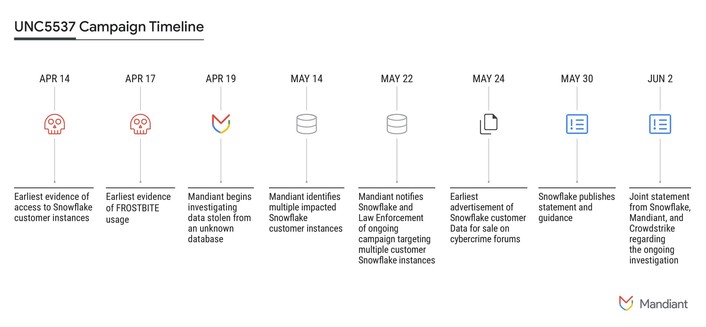
Mandiant have informed 165 organisations they may have had data exfiltration from their Snowflake hosted databases
https://cloud.google.com/blog/topics/threat-intelligence/unc5537-snowflake-data-theft-extortion/
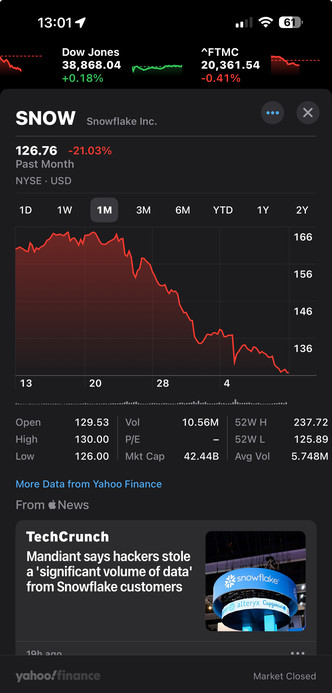
Kinda interesting - Mandiant notified Snowflake that over 100 customers had data exfil issues, and Snowflake’s share price immediately began to tank in sells offs - before the incident was made public.
won a game of Call of Duty
hacked the world’s largest companies
used an infostealer
Can’t wait for these guys to have super secure Microsoft Recall, which is definitely encrypted from the user
Snowflake have told customers "We are also developing a plan to require our customers to implement advanced security controls, like multi-factor authentication (MFA) or network policies, especially for privileged Snowflake customer accounts."
Good! They also say the attack was "not caused by a vulnerability, misconfiguration, or breach of its product". Just happy little bad MFA.
Nice: "In a phone call this week, Jones (Snowflake CISO) told WIRED that Snowflake is working on giving its customers the ability to mandate that users of their accounts employ multifactor authentication going forward, “and then we’ll be looking in the future to [make the] default MFA,” he says."
This will be a great outcome for Snowflake customers and Snowflake itself. I know Snowflake got big mad at me for pointing it out, but that was a prime weakness in their MFA.
https://www.wired.com/story/epam-snowflake-ticketmaster-breach-shinyhunters/
The Hudson Rock blog earlier in this thread on Internet Archive has also been removed. https://web.archive.org/web/20240531140540/https://hudsonrock.com/blog/snowflake-massive-breach-access-through-infostealer-infection
The Hudson Rock blog on Snowflake, archived elsewhere: https://archive.ph/2024.06.01-023241/https://www.hudsonrock.com/blog/snowflake-massive-breach-access-through-infostealer-infection
65 page PDF on searching for Snowflake malicious activity: https://services.google.com/fh/files/misc/snowflake-threat-hunting-guide.pdf
When Snowflake allows orgs to easily mandate MFA across their users, I plan to answer this forum post from 2019. https://community.snowflake.com/s/question/0D50Z00008ugjwISAQ/is-there-a-way-to-force-all-users-to-use-mfa
Cisco has a look across the wider infostealer problem, using Snowflake as a jumping off point: https://blog.talosintelligence.com/infostealer-landscape-facilitates-breaches/
I think SaaS providers who provide their own authentication have a responsibility to provide robust, *enforceable* MFA for their customers - so if an org wants all their users to require MFA, they can and it’s just an easy tick box.
Some SaaS providers aren’t doing this - - and it’s the reason infostealer logs are such a problem. Their angle is customer is solely responsible, but as a counterpoint: see how that is working out for Snowflake.
Snowflake have rolled out MFA changes:
- A new authentication policy that requires MFA for all users in a Snowflake account
- prompting for user-level MFA setup
- Snowflake Trust Center for monitoring adherence to MFA policies
This solves all the inherent product weaknesses from the prior setup, they did a good job.
https://www.snowflake.com/blog/snowflake-admins-enforce-mandatory-mfa/
AT&T become latest org caught up in Snowflake incident - they’ve had phone call records and text messages stolen for nearly all customers. https://www.404media.co/hackers-steal-text-and-call-records-of-nearly-all-at-t-customers/
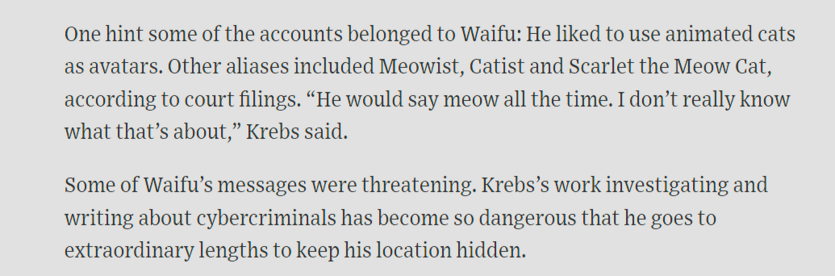
The person who got arrested for this is likely a kid btw, there’s a bunch on Telegram who operate with terrible OPSEC.
Turns out yeeting your most sensitive data into a “AI Data Cloud” with no enforceable (at the time) MFA was a bad idea.
An observation - AT&T, which today announced the biggest data breach of any telco worldwide ever - is down 0.35% on stock market
Snowflake, who own the SaaS platform, are down another 2%, 15% down over 3 months
Each breach has driven Snowflake’s share price down, but not their customer’s share price
In other words: 2024 reality, if you’re a SaaS provider, infostealers and cyber crime groups are a competitor - you have to be shit hot at authentication (even if it inconveniences the customer)
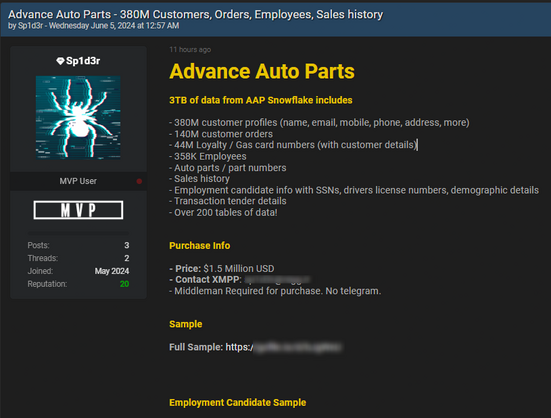
Advanced Auto Parts have confirmed 2.3 million people impacted in their Snowflake breach. https://www.helpnetsecurity.com/2024/07/12/breach-snowflake-mfa/
The AT&T Snowflake database wasn’t a law enforcement database, that is false.
They’re a major Snowflake customer, they put CDR in to do data analysis.
They subscribe to Snowflake Telecom Data Cloud and push petabytes of data in, as do other telcos. Snowflake had no way to mandate MFA on local accounts (that is fixed now).
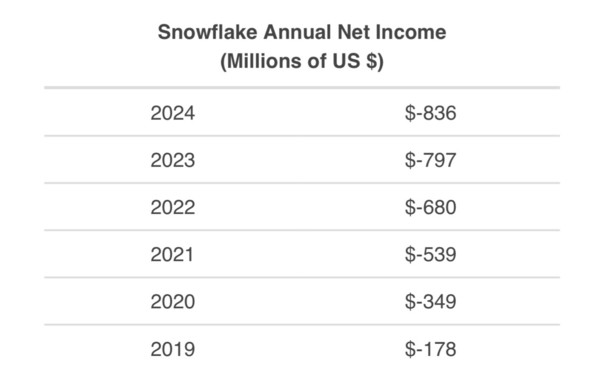
The latest Snowflake quarterly results dropped on Wednesday so I looked at their investor presentation, to see what they said about the security incident.
Nothing.
The company's net loss widened to $317 million, from $227 million during the same period a year earlier but this isn’t unusual, they have had accelerated losses for some time.
More smart changes by Snowflake
MFA enforced on all accounts and all new sign ups
Long term plan to go passwordless for authentication (or rather no single factor password auth)
https://www.snowflake.com/en/blog/multi-factor-identification-default/
Paywall'd article, but a fun look at infostealers and how they played a part in the Snowflake happy little cyber incident earlier this year https://www.404media.co/inside-the-massive-crime-industry-that-is-hacking-billion-dollar-companies-copy-2/
The alleged Snowflake hacker behind the 160 odd happy little cyber incidents has been arrested in Canada. If it’s him he probably shouldn’t have admitted it to a reporter. https://www.404media.co/suspected-snowflake-hacker-arrested-in-canada/
there's so many wtf moments in this story about the alleged Snowflake hacker, lol
https://krebsonsecurity.com/2024/11/canadian-man-arrested-in-snowflake-data-extortions/
I should loop this in for more crazy on the Snowflake non-incident incident, where a bunch of teens ran around the poor security at both Snowflake and Snowflake's customers.
https://www.wsj.com/tech/cybersecurity/hacking-brian-krebs-snowflake-waifu-49b87fce?st=Pubz4o
Boggles the mind that nation state China managed to get into various US telcos.. and so did a 20 year old kid, who had to be doxxed by @briankrebs to even get arrested.
I'm hoping this one goes to trial so the feds are forced to reveal what happened - as I understand it, various telcos exported CDRs - call record data - and put it into Snowflake Telco Cloud, which didn't have a feature to require MFA for every telco user account, and some users forgot to enable it.
https://krebsonsecurity.com/2024/12/u-s-army-soldier-arrested-in-att-verizon-extortions/
@GossiTheDog Snowflake might be the easiest way to analyze CDRs in anything like a reasonable period of time. They're horrendously chatty.
@GossiTheDog CDR stands for?
@GossiTheDog Is it really a security incident though? There was no evidence snowflake itself was breached
Eh, I feel like "incident" is more broadly encompassing than "breach", and I'd suggest systematically weak service provider security controls that allowed large scale compromise of their customers' data should qualify as an incident for the service provider.
@malwaretech @GossiTheDog every SaaS/retail/social company that offers services to the general public deals with cred stuffing/valid cred attacks on a daily basis.
Is it their fault the user synchronizes or exposes their creds? No. Should they have monitoring and logging in place and give users the ability to mandate 2FA or create narrowly scoped OAuth tokens? Yes.
So is it a security incident? Yes, unauthorized access. Is it their fault? A bit?
@GossiTheDog well, yeah, that’s because board rooms absolutely do not give a shit about cyber security unless they are a cyber security company (and even then it’s marginal interest at best)
@GossiTheDog I got a LinkedIn invite from Snowflake just 2 days ago to a webinar they were running on cybersecurity. I'll give them credit, they've got chutzpah.
@GossiTheDog In the earnings call, Ramaswamy mentioned it during the opening, if only to reiterate that it wasn't an internal breach. He also implored customers to enable MFA
@GossiTheDog this passwordless thing is the email with the magic link, like StreamYard?
@guelfoalexander @GossiTheDog probably passkeys/FIDO2.
@markeldo sorry thats even worse to me. you need to have 2 or more of such devices (if you loose them or simply forget them at home), possibly one in a safe and one of your wife in which you cross store the recovery passwords/passkeys and if you are a dumbster like me having too many levels of security gets you to bypass them in order not to waste time. remember that https://www.tumblr.com/bluebigcat/637569302145515520/ieri-quello-che-%C3%A8-successo-a-google-non-%C3%A8-stato?source=share
(for non italian speking folks please use a translator)
@guelfoalexander it’s a better solution for most people. And you can store passkeys in iOS or Android and they will sync to your devices.
@markeldo you see it, thats NOT passwordless, that passwordtoomany
@guelfoalexander it’s passwordless. There’s no password.
@markeldo oh sorry. passkeytoomany
@GossiTheDog Bragging about his OPSEC to a security researcher is pretty funny.
@GossiTheDog @briankrebs
All your data are belong us.
@GossiTheDog "I've destroyed a lot of evidence" is definitely a good thing to say to a reporter as the law is closing in!
(It puts a smile on the face of the DOJ attorney as they paste the screenshot into their filing, which can only work in your favor)
@GossiTheDog fuck your paywall. If this is important let me see it. If not fuck off.