Recent searches
Search options
Microsoft quietly snuck out a blog yesterday to say that Office 365 got compromised by China and used to steal emails. Thread follows. https://msrc.microsoft.com/blog/2023/07/microsoft-mitigates-china-based-threat-actor-storm-0558-targeting-of-customer-email/
They used Outlook Web App - runs the Exchange Server codebase btw - to craft tokens to bypass auth.
There's some clever wording in blog around only impacting OWA. OWA is a part of Microsoft 365 and Exchange Online.
The problem was discovered by the US Government and reported to Microsoft. https://edition.cnn.com/2023/07/12/politics/china-based-hackers-us-government-email-intl-hnk/index.html
Microsoft have not linked the blog on @msftsecintel or @msftsecresponse Twitter accounts or social media, instead linking pieces yesterday about an unrelated phishing campaign.
This one looks like a huge mistake, a consumer MSA key (managed end to end by Microsoft - there's no external logs) was able to forge any Azure AD key.
It's only become public it appears as the US Government told Microsoft, which forces public disclosure.
Although MS haven't called this a vulnerability, haven't issued a CVE or used the term zero day.. they don't issue CVEs for cloud services, forging a token is a vulnerability, so it's a zero day.
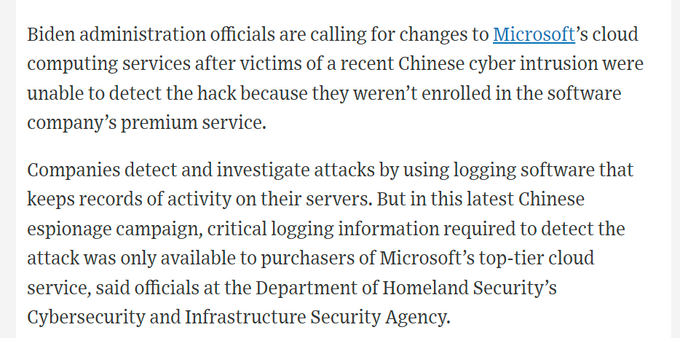
CISA's advisory on the Microsoft 365 compromise is wayyyyyyyyyyy better than the Microsoft advisory - contains actionable hunting and logging information. Kinda nuts that the US Government are providing better information about Microsoft than Microsoft.
Another element - to spot this activity, the US government used enhanced logging aka Purview Audit (Premium) logging - the US government had a huge public fight with Microsoft over this a few years ago over cost, to get access. Turns out they needed it indeed.
Does anybody have the AppID used in the Microsoft 365 compromise? -> kevin.beaumont@gmail.com
WSJ reporting the Microsoft 365 hack was used to spy on the State Department. https://www.wsj.com/articles/chinese-hackers-spied-on-state-department-13a09f03
For anybody interested - the “acquired Microsoft account (MSA) consumer signing key” used in this must have come from inside Microsoft’s internal network.
The teams who worked on the Microsoft 365 breach of customer data are having a snow day still, I see.
Okay - I found a victim org.
The situation for them is
MS are going to have to release more info, methinks.. or I crank out the blog writing.
Really good Washington Post piece on the breach of Microsoft 365’s email service.
- hackers accessed customer emails for a month
- Microsoft didn’t notice
- USG had to tell them
- The access to generate tokens very likely came from MS being hacked and not realising
None of these would have helped, since the breach was at Microsoft’s end.
Talked to another impacted victim org in the Microsoft 365 hack, they basically got no actionable info from MS. Basically ‘lol you got hacked’ with wordsmithing and padding.
I think I’m going to post hunting queries for this with an MS Paint logo.
regulation
I agree with CISA here (and have publicly for years) - security access logs for customers own services shouldn't be locked behind E5 per user licensing.
Yes, it will cost Microsoft money in upsell. They're more profitable than a large portion of the UK economy; they can afford it.
I should also point out the reason Microsoft was able to tell orgs specifically that they'd be targeted even when they didn't have E5 is MS already store the logs anyway.
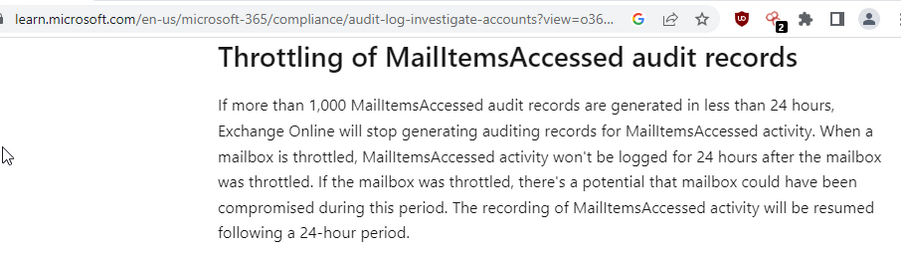
On how the USG, European govs and Microsoft have been threat hunting the MS 365 breach, per Microsoft documentation on the logs... "If a mailbox is throttled, you can probably assume there was MailItemsAccessed activity that wasn't recorded in the audit logs."
Really good new MS blog on the MS compromise - contains IOCs etc. I'll put MSPaint.exe down. https://www.microsoft.com/en-us/security/blog/2023/07/14/analysis-of-storm-0558-techniques-for-unauthorized-email-access/
“We don’t have any evidence that the actor exploited a 0day." say Microsoft. Their first blog on this says “exploit” - so are MS saying they don’t patch vulnerabilities in their cloud?
Their latest blog also says “This was made possible by a validation error in Microsoft code” - which is a vulnerability. Which is a 0day as it was under exploitation before Microsoft knew of it existing.
Microsoft lying to media and customers is not a good look.
All it took was Exchange Online in GCC and GCC High getting breached
Non-E5 users to get some security log availability finally.
More details about the Microsoft 365 Exchange Online breach in this article.
Although not stated, orgs are struggling to understand the scope of the breach due to audit log limits on MailItemsAccessed - it stops recording after 1k items. https://www.wsj.com/articles/u-s-ambassador-to-china-hacked-in-china-linked-spying-operation-f03de3e4
Just to loop this thread into this thread - I took a look at the attack path used in the M365 customer data breach.
A key part of the attack chain was documented by Microsoft at BlackHat in 2019.
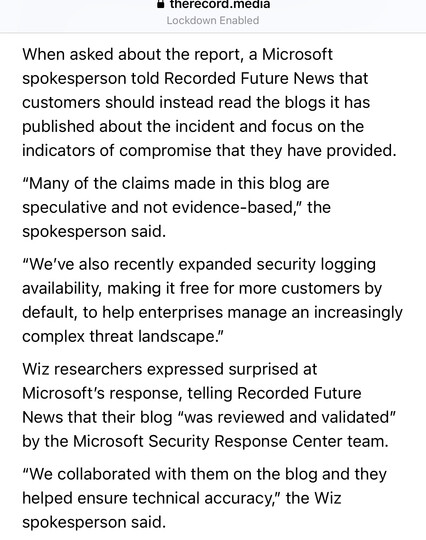
Wiz have an in-depth look at what they think happened at Microsoft over the Microsoft 365 breach.
They nail a new detail - one of the 'acquired' signing keys expired in 2021, but apparently it was still valid in Microsoft's cloud services. https://www.wiz.io/blog/storm-0558-compromised-microsoft-key-enables-authentication-of-countless-micr
YOU MUST ONLY READ THE OFFICIAL BLOGS
there is no breach
there is no vulnerability
there are no zero days
*jedi wave*
https://therecord.media/microsoft-disputes-report-on-chinese-hacking
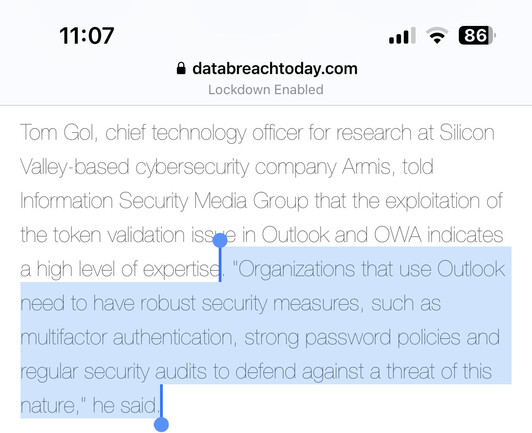
@GossiTheDog Good grief. Sounds like ole Tom might be a proponent of the security-by-checklist approach so many big orgs live by.
@GossiTheDog I *hate* using security features as an upsell opportunity instead of a baseline requirement. Years ago Auth0 quoted us more for 2FA for identity users - I pushed back hard (and made it clear that they would be named in any breach comms), and they capitulated.
@cfg @GossiTheDog thank you for your service
Same article but just in case they edit or you're a scrub like me
@GossiTheDog Reminds me of the incident in the late 90's where Microsoft created a public server-validation certificate that expired before its creation-date... approx 100 years before, to be sure.