Recent searches
Search options
Been looking at Microsoft 365 email breach some more - it looks like Microsoft were aware of issues in same token validation space in Exchange Online 4 years ago.
MS did a talk at BlackHat about it, after somebody external pointed out an invalid token allowed any email box to be accessed via consumer Outlook.com.
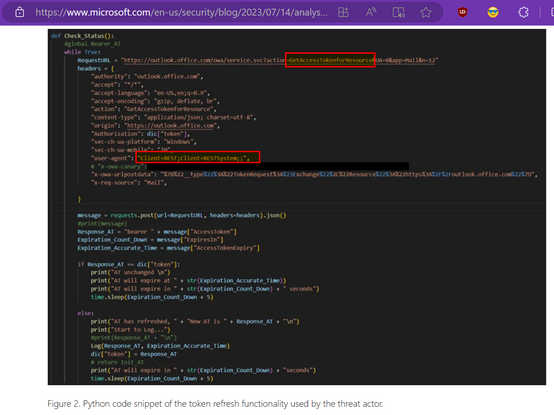
They fixed that issue - but still allowed any valid MS token to access any email, so the threat actor stole one of the MSA certs.
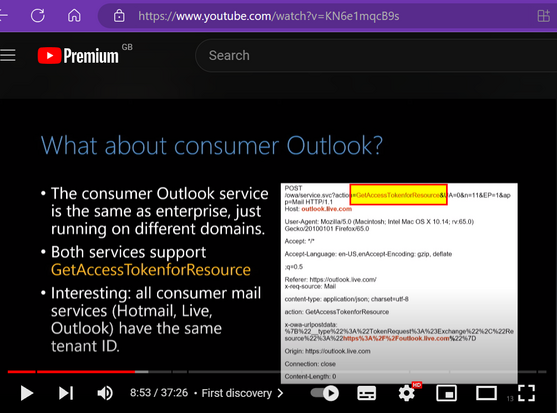
Somebody definitely went back and looked at this methinks, as the threat actor pulled the AppId they're using from JWT on consumer Outlook.com (not in the talk) which gave them additional access. So there's a lot of complexity there, too much to fit in a toot.
I do think MS need to have a 'bring out the dead' session with their security red teams at some point - this one is spottable.
Relying on friendly security researchers isn't going to work in cloud. $40k bounty on OG find, lol.
This thread in GIF form.
This one is 100% code written by MS in products owned by MS in services owned by MS... the castle needs to be slightly more robust. And by slightly I mean definitely. Hindsight's a wonderful thing, but I guess it's an opportunity to empty out the skeletons in the closet.