Recent searches
Search options
3 different VMware zero days, under active exploitation by ransomware group
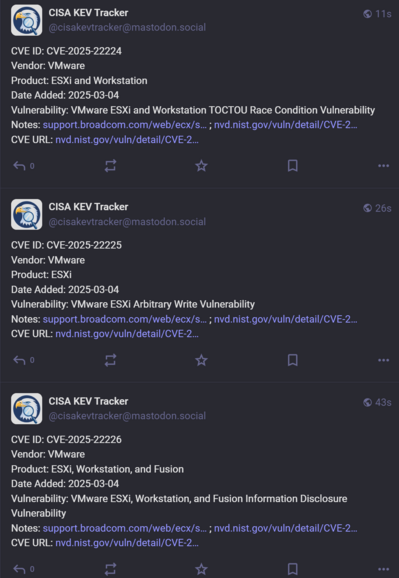
CVE-2025-22224, CVE-2025-22225, CVE-2025-22226
VMware ESXi
VMware Workstation Pro / Player (Workstation)
VMware Fusion
VMware Cloud Foundation
VMware Telco Cloud Platform
(Exploitation actually ESXi)
You may want to escalate patching this as it allows virtual machine to hypervisor escape - e.g. from some dumb VM to the whole VMware private cloud estate.
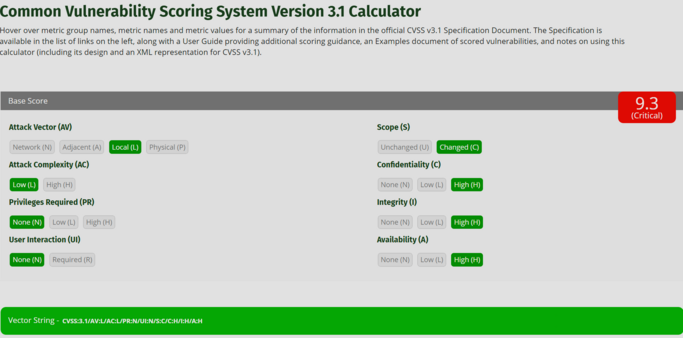
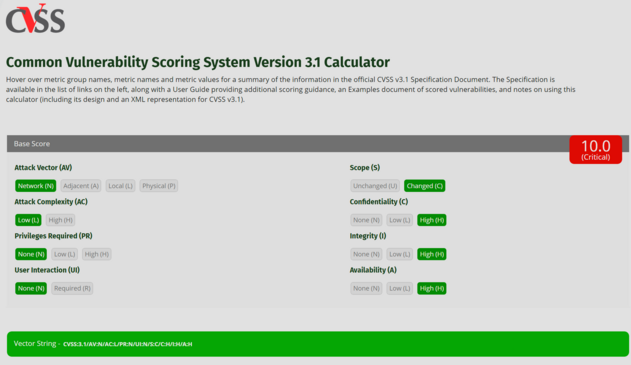
VMware have set the Attack Vector to Local, which brings down the CVSS score - but you don't need to be locally at a VM to do the attack, you can do it over the internet if you have access to any VM.
If you change it to Network, you get 10
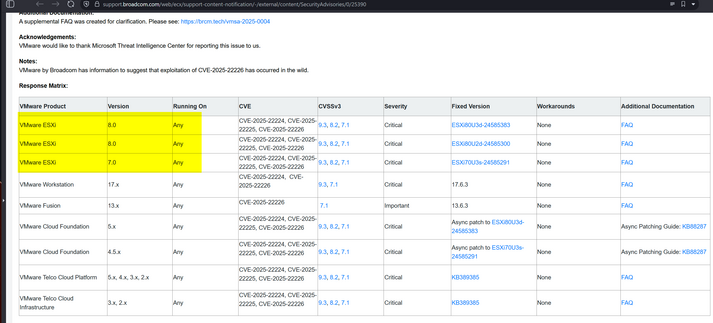
Good catch by @TomSellers - although VMware doesn't list ESXi 6.7 as vulnerable, it is - they've published a patch for it: https://techdocs.broadcom.com/us/en/vmware-cis/vsphere/vsphere/6-7/release-notes/esxi-update-and-patch-release-notes/vmware-esxi-67-patch-release-esxi670202503001.html
I think what's happening here is 6.7 is under premium (paid) extended support where they publish patches for high severity vulns for $$
This also tends to indicate it applies to other unsupported versions. The forum post suggested that vuln worked on ESXi 5.x - no patch is available that far back.
I think this may be a big problem for many orgs.
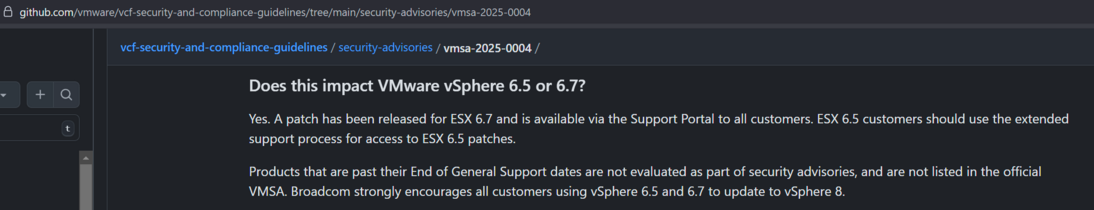
Another good catch by @TomSellers - VMware's website advisory has less detail than their github for some reason.
Their github: https://github.com/vmware/vcf-security-and-compliance-guidelines/tree/main/security-advisories/vmsa-2025-0004
According to their Github, additional VMware ESXi versions are impacted (e.g. 6.5, 6.7) and older versions are likely impacted but no patches available.
An in the wild exploit for RCE hypervisor escape across every supported (and unsupported) product like this is unprecedent.
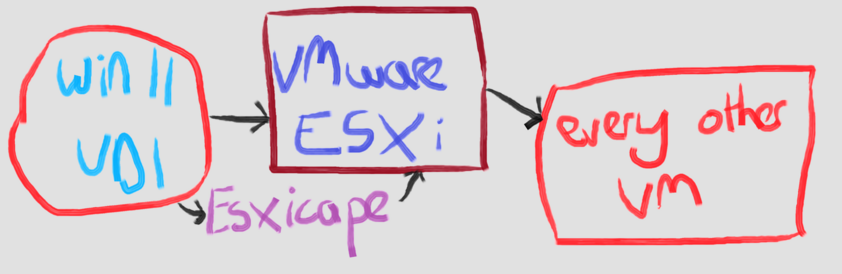
Quick mspaint.exe diagram on this, calling it ESXicape
- Have access to something like a Windows 11 Virtual Desktop system in VMware, or a Linux box or some such?
- Use ESXicape, a chain of three zero days, to gain access to the ESXi Hypervisor.
- Use that to access every other VM, and be on the management network of VMware cluster
One you have this level of access, traditionally you'll see groups like ransomware actors steal files and wipe things. #ESXicape
Does anybody know anybody at VMware Security who could have a look at the #ESXicape knowledge base article please?
It's missing 6.5 and 6.7, which are definitely vulnerable and have patches available on Broadcom's site. They're also listed in the VMware Github advisory, but have been missed off the support site. It's causing people to not patch.
Both VMware and Microsoft have declined to comment about #ESXicape, when asked about number of victims and who has the exploit.
A new twist on #ESXicape - you need local admin rights to escape the VM to the hypervisor, right?
Slight issue - VMware Tools, installed inside VMs, allows local user to local admin privilege escalation on every VM due to vuln CVE-2025-22230
“A malicious actor with non-administrative privileges on a Windows guest VM may gain ability to perform certain high-privilege operations within that VM.”
Discovered by Positive Technologies, who US claim hack for Moscow.
@GossiTheDog
The answer is “yes”.
@GossiTheDog thereby confirming it’s not going to be a good time for many