Recent searches
Search options
Microsoft released a blog this week which I don’t think people have fully understood the implications of, but it’s great research and a great attack by the threat actor.
I think it’s highly likely multiple threat actors will now jump on this, it’s even automatable.
The attack:
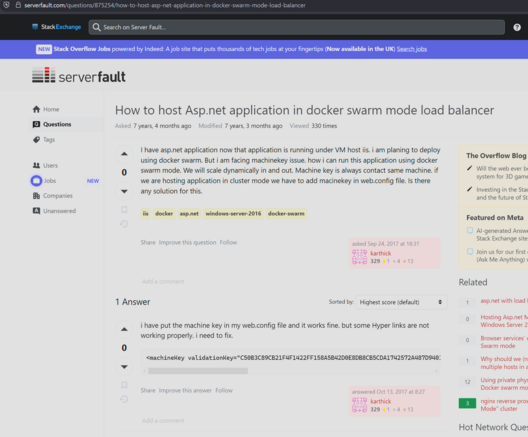
1) take a web.config file. They’re really easy to find.
2) POST request to RCE in IIS
The architecture of .net means this is surprisingly easy to do and you don’t patch your way out of it.
I’ve bookmarked this thread so it doesn’t auto delete the toots, put it that way. You could just automate spraying the internet with this one.
https://github.com/projectdiscovery/nuclei-templates/blob/2390fd195ab00f2bb1142dd27ac2ab888622d9bd/http/exposures/configs/web-config.yaml#L22
@GossiTheDog o_O what in hades is this abomination?
@GossiTheDog Ah viewstate, best of intentions and the worst of implementations
https://web.archive.org/web/20101225182433/http://netifera.com/research/poet//PaddingOraclesEverywhereEkoparty2010.pdf
Similar attacks can be executed against frameworks that also protect stateless session data with encryption/MAC's, see CVE-2018-15133 of Laravel:
https://mogwailabs.de/en/blog/2022/08/exploiting-laravel-based-applications-with-leaked-app_keys-and-queues/
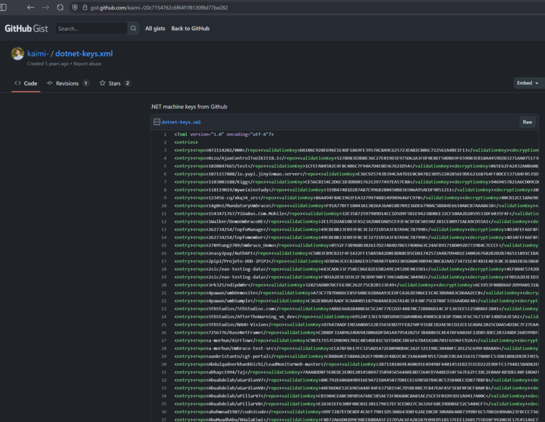
We've been hunting for web.config's during pentests too - the latest exploit I remember must've been written around last December by teammate based on a file read vuln exposing web.config.
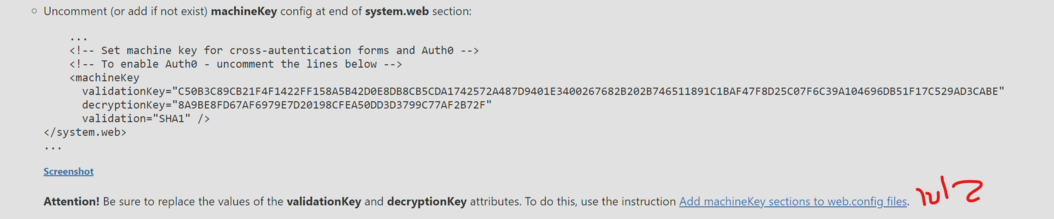
So yeah, don't expose your private keys... If you do, that's not the problem of the crypto system (or ASP.NET in this case).
@buherator @GossiTheDog There's long list of "default" secret keys used for JWT and session cookies collected in various github projects. Similarly on Ruby on Rails, Django the secret session key can lead to RCE through unmarshalling. JWT can give you admin role etc.
@GossiTheDog MS Defender alerts if it finds configs with those leaked keys. Quite useful
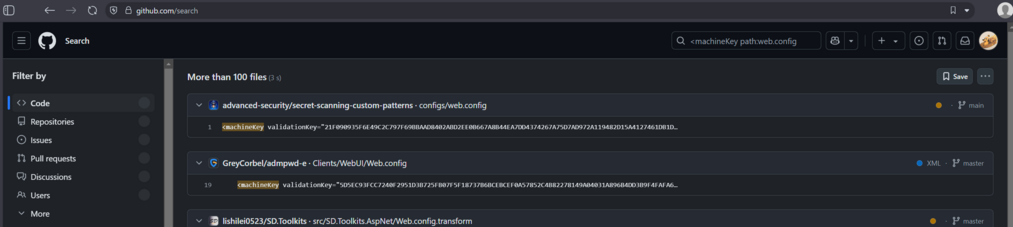
Also, TIL you can use boolean expressions, e.g. you can filter for autogenerated keys:
https://github.com/search?q=%3CmachineKey+validationkey+path%3Aweb.config+NOT+autogenerate&type=code
@buherator @GossiTheDog Yep, quite a few CTF repos in here.