Recent searches
Search options
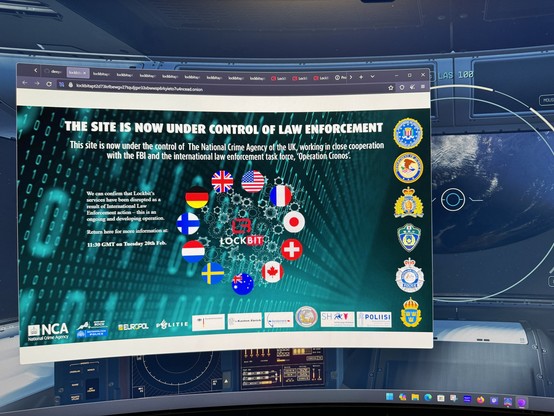
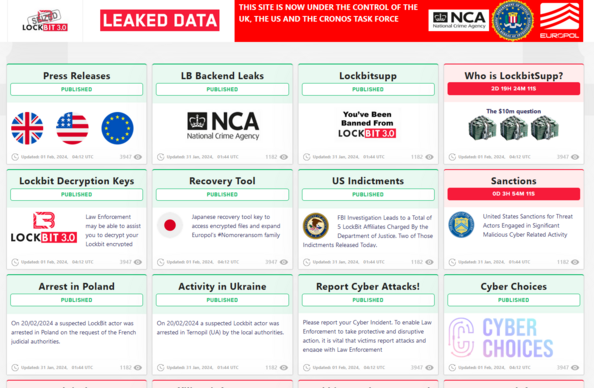
HT to @brett, apparently LockBit 3.0’s site has been seized by the NCA.
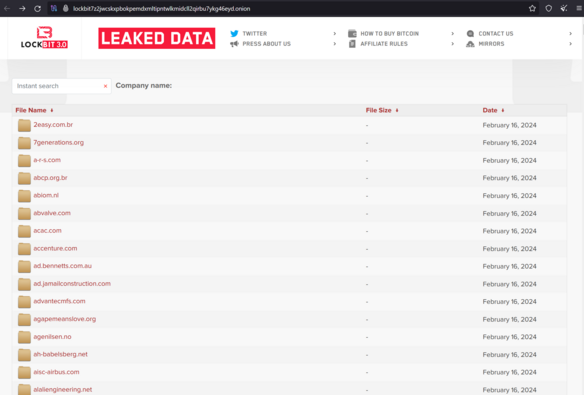
If real, the NCA should note the leaked data, file share and private note servers and portals are still online. #threatintel
LockBit are offline on instant messaging, y'all will be surprised to know.
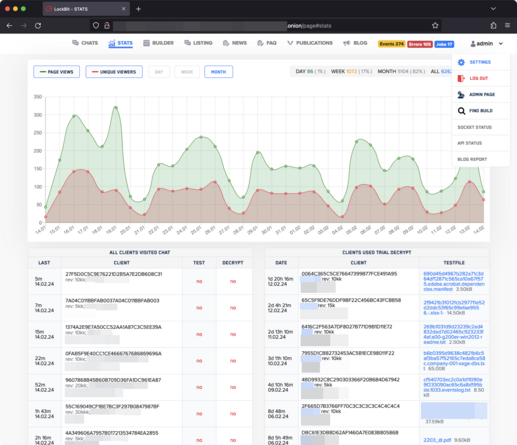
LockBit still have infrastructure online, which is still counting up in terms of uptime.
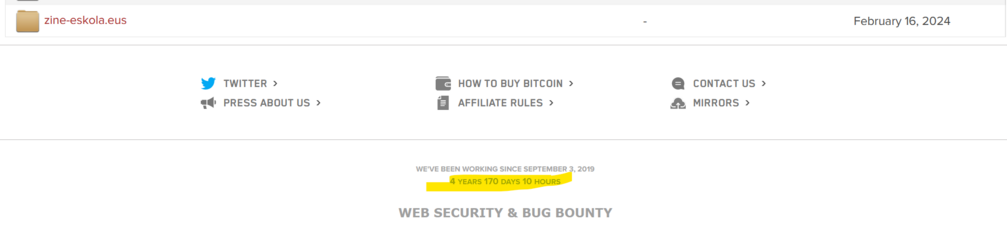
It's pretty mind boggling to me that for 4 years 170 days, these guys have been doing horse carriage robbery of schools and hospitals and.. uh... they just did it.
(Also, yes, they have a bug bounty that pays better than most large orgs).
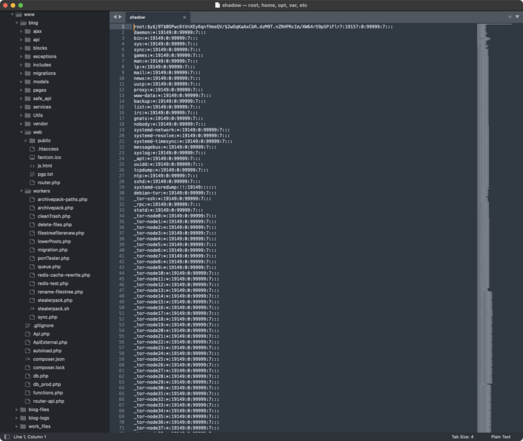
Just to be super clear, 3 different LockBit services are still online:
http://lockbit7z2jwcskxpbokpemdxmltipntwlkmidcll2qirbu7ykg46eyd.onion/
http://lockbitfile2tcudkcqqt2ve6btssyvqwlizbpv5vz337lslmhff2uad.onion/
http://lockbitnotexk2vnf2q2zwjefsl3hjsnk4u74vq4chxrqpjclfydk4ad.onion/
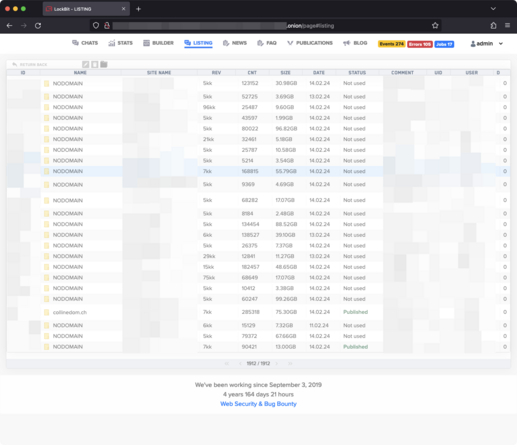
The first one is still serving stolen data, so if law enforcement have taken control of the infrastructure they definitely need to shut that one down.
if you want to hack ransomware groups, I pay tax so you can: https://www.gchq.gov.uk/news/national-cyber-force
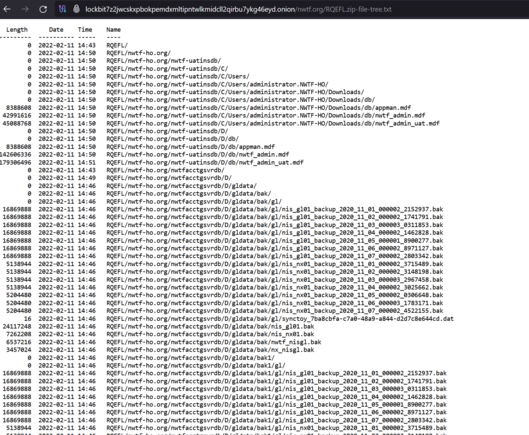
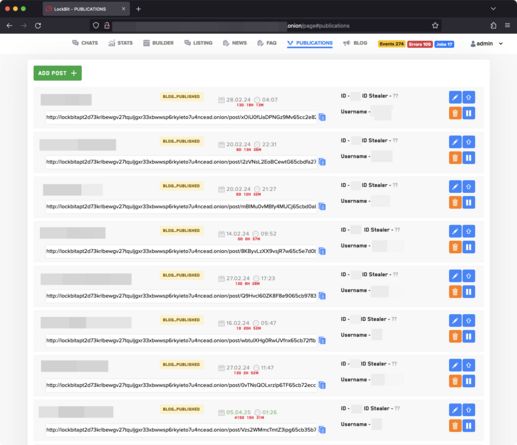
So there's loads more to come on the LockBit takedown, including new info on how they exfiltrate data and such.
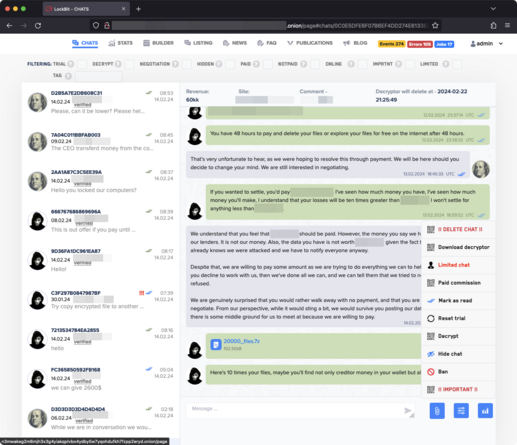
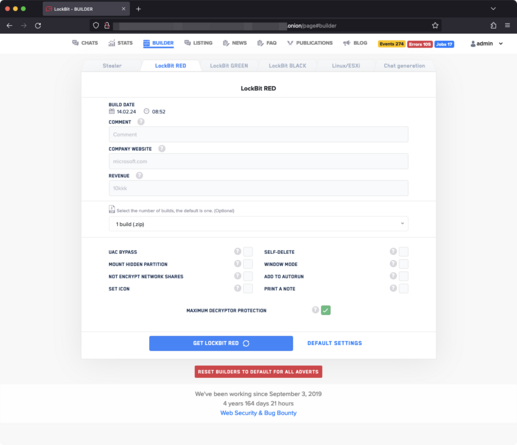
One extra bit of info - even after companies paid the ransom, LockBit were keeping the data - it was on the servers the NCA seized.
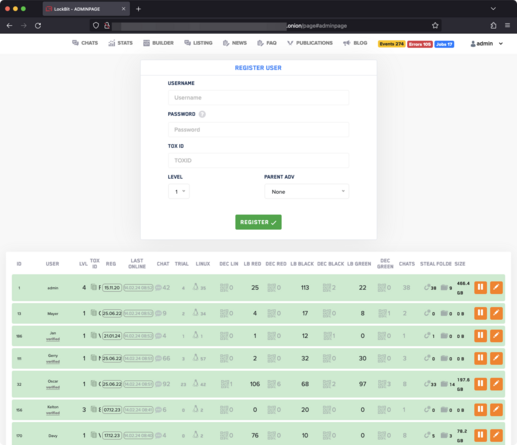
All the companies who told the ICO and EU regulators their data had been “secured” after paying ransomware groups
@GossiTheDog I am so very very surprised.
@GossiTheDog double extortion works, heh.
@GossiTheDog fry shocked dot gif
@GossiTheDog I just wonder if any of the affected orgs are otherwise under investigation and if getting these dumps *not from the companies themselves* is legal for the investigators...... And if the info would be admissible, only relevant to show where admissible copies could be found, or considered poisoned.
@GossiTheDog Wait, they are not IEC 27001:2022 compliant?




 Why Not Zoidberg?
Why Not Zoidberg? 