Recent searches
Search options
ArcticWolf are reporting "Qlik Sense Exploited in Cactus Ransomware Campaign" https://arcticwolf.com/resources/blog/qlik-sense-exploited-in-cactus-ransomware-campaign/
Thread time as there's some additional detail I want to add:
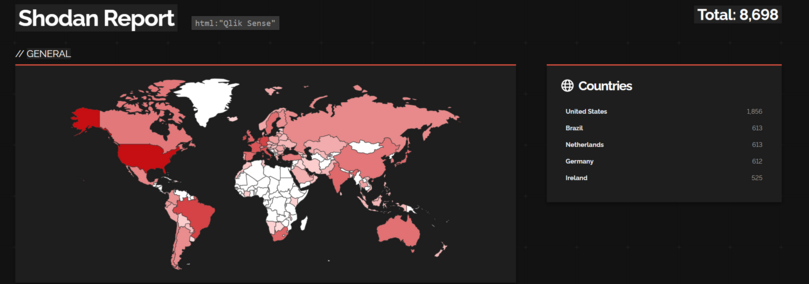
From @shodan we can find Qlik Sense is heavily deployed in the US. It's a range of industries.
It also has a footprint in government.
It is expensive data analytics software, with a webapp.
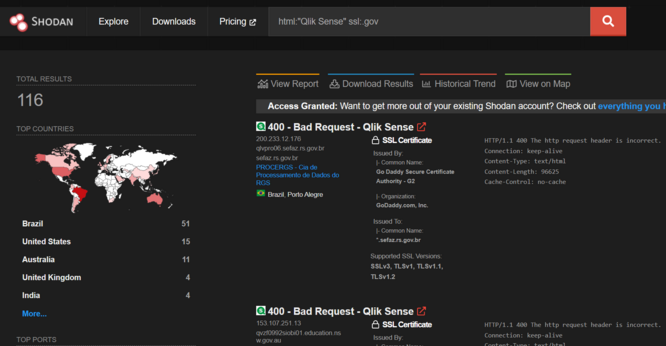
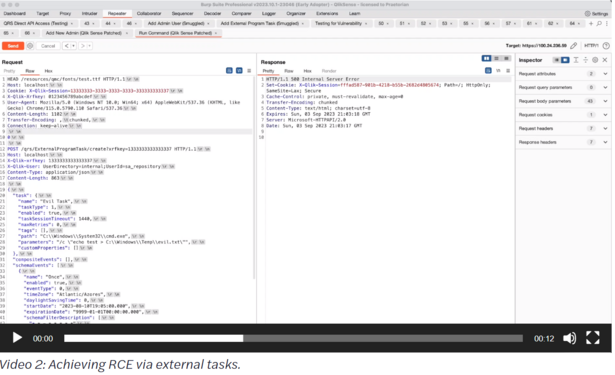
The Qlik Sense vulns were discovered in August and September by Praetorian, an InfoSec vendor - unfortunately they published a full exploit chain, which the ransomware group has lifted wholesale.
Their stated intention was "..proactive vulnerability research focused on finding critical issues before attackers can identify and exploit them" https://www.praetorian.com/blog/qlik-sense-technical-exploit/
Cactus is a ransomware group to watch. Most of their victims don't end up on their portal - e.g. Lyca Mobile got hit a few months ago and paid to avoid scrutiny.
They're clearly paying attention to vulnerability researchers.
I’ve seen another ransomware group exploiting Qlik Sense. Currently it is a very low number of attacks so you might want to patch. #threatintel