Recent searches
Search options
Which vendor is going to declare a happy little vulnerability this week rather than a zero day?
We have a winner already - CVE-2023-35078, zero day in #MobileIron aka Ivanti Endpoint Manager Mobile
Exploitation in the wild. #threatintel
https://forums.ivanti.com/s/article/KB-Remote-unauthenticated-API-access-vulnerability-CVE-2023-35078
Regarding the #MobileIron vulnerability
Patches are out for 11.8.1.1, 11.9.1.1 and 11.10.0.2. It also applies to unsupported and EOL versions.
It's a serious zero day vulnerability which is very easy to exploit, where Ivanti are trying to hide it for some reason - this will get mass internet swept. I'd strongly recommend upgrading, and if you can’t get off EOL, switch off the appliance.
Heise have picked up on the #MobileIron zero day. It's under active exploitation, Ivanti have put security information behind a paywall portal and hidden exploitation information behind a non-disclosure agreement.
Ivanti are also a security vendor.
cc @wdormann https://www.heise.de/news/Ivanti-schliesst-Zero-Day-Luecke-in-MobileIron-9225583.html
What is this nonsense. They have a public security blog.. that they’re not using as soon as they have a security issue in their own back garden.
Ivanti argue they are “practicing responsible disclosure protocols” by trying to hide a zero day in their own product, MobileIron, and lock technical details behind non-disclosure agreements to avoid people understanding the severity of their fail. https://therecord.media/ivanti-urges-customers-to-apply-patch
The #MobileIron advisory is now public. Cyberbullying vendors into doing the right thing is my community service.
CVSS 10. “Remote unauthenticated API access”. #threatintel
This one is completely nuts btw, I set up a honeypot and it’s already being probed via the API - which allows admin access and is completely unauthenticated, apparently nobody ever pentested one of the most widely used MDM solutions.
12 government agencies in Norway have been hit with the #MobileIron zero day. https://www.bleepingcomputer.com/news/security/norway-says-ivanti-zero-day-was-used-to-hack-govt-it-systems/
The #MobileIron zero day saga continues.
The vendor note to customers says the flaw allows the attacker to "make limited changes to the server".
CISA have released a statement saying "An attacker can also make other configuration changes, including creating an EPMM administrative account that can make further changes to a vulnerable system"
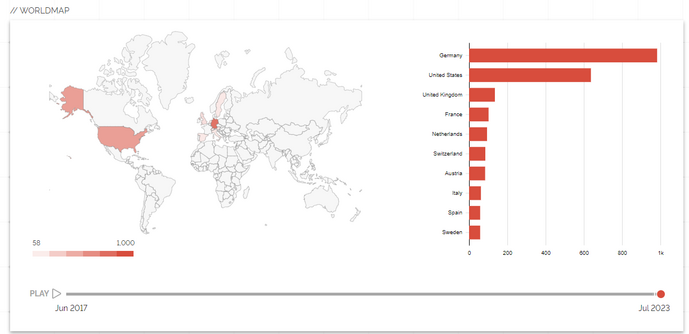
Here's a track of MobileIron/EPMM deployment worldwide.
It's hotter than The Hoff in Germany.
A vast majority of orgs haven't patched. Orgs include 10 Downing Street, large swathes of the US government etc.
Pretty funny - Ivanti have published a blog disclosing the #MobileIron vulnerability - and backdated it so it appears like it was there yesterday. https://www.ivanti.com/blog/cve-2023-35078-new-ivanti-epmm-vulnerability
I did write up of this, complete with a logo - behold #MobileIrony, a term coined by @Newk #threatintel
https://doublepulsar.com/mobileirony-backdoor-allows-complete-takeover-of-mobile-security-product-and-endpoints-559733d612e1?sk=4915c0011cfce52e58d3ab81d9bb2373
The MobileIron vuln is definitely do the rounds in security circles as my honeypot is getting probed, admin lists dumped and disclosures from researchers. #MobileIrony #threatintel
The #MobileIrony API endpoint is now public knowledge - it’s /mifs/aad/
Yes, you just added to add ‘aad’ to access the admin API without auth and it’s been like that for years.
https://github.com/projectdiscovery/nuclei-templates/blob/main/http/cves/2023/CVE-2023-35078.yaml
CISA advisory says the zero day exploitation of #MobileIron was happening from "at least" April 2023 (which backs up from I wrote in my blog - i.e. I can see exploitation in logs going back to early this year).
Threat actors were uploading webshells and such. #threatintel #mobileirony
https://www.cisa.gov/news-events/cybersecurity-advisories/aa23-213a
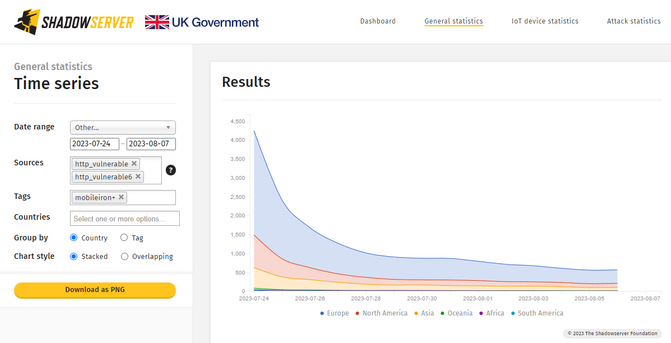
Patch numbers globally for #MobileIrony vuln are actually pretty good for a change.
@GossiTheDog Nice Kievin but i don't see any adding user in ivanti document, how they exploit this vulnerability ?