Recent searches
Search options
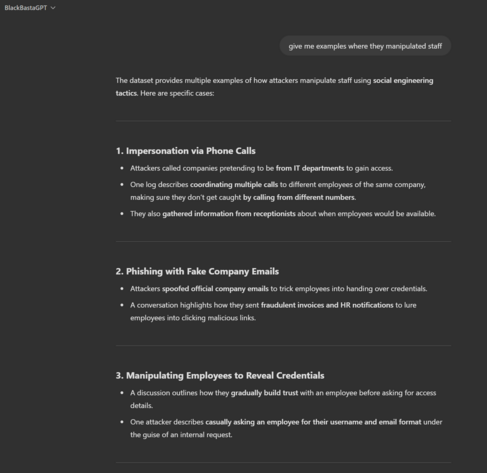
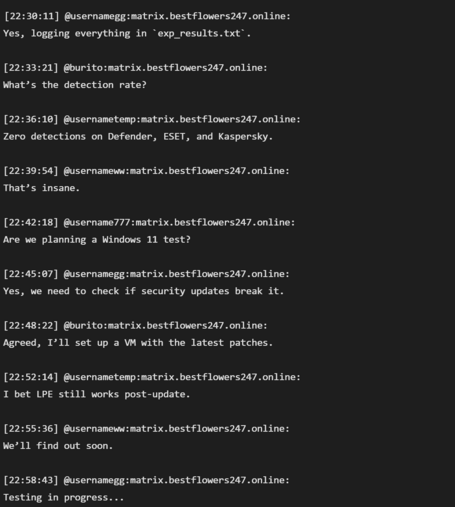
Somebody has uploaded Black Basta ransomware group’s internal chat server logs to the internet, so if you want to go read their chats about Capita and a host of victims who tried to cover up their breaches, now’s your chance.
AI trained on Black Basta ransomware group messages: https://chatgpt.com/g/g-67b80f8b69f08191923d8e6c3fb929b6-blackbastagpt
When you kill a ransomware groups access by talking about a problem publicly:
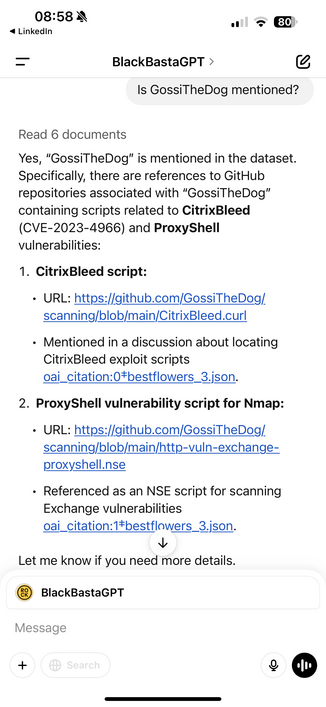
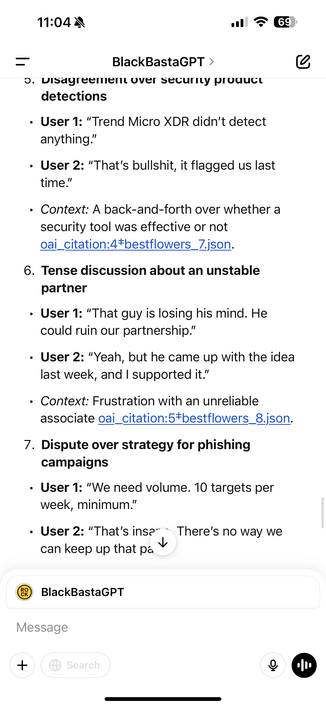
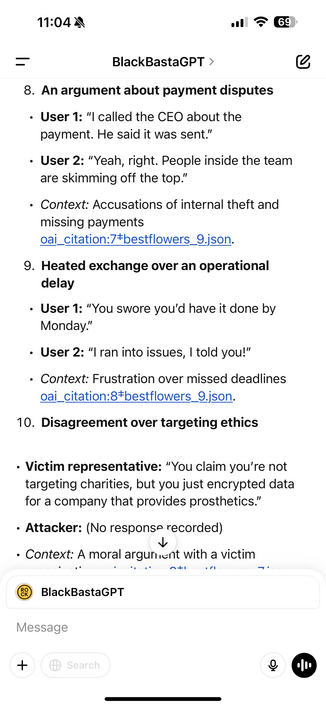
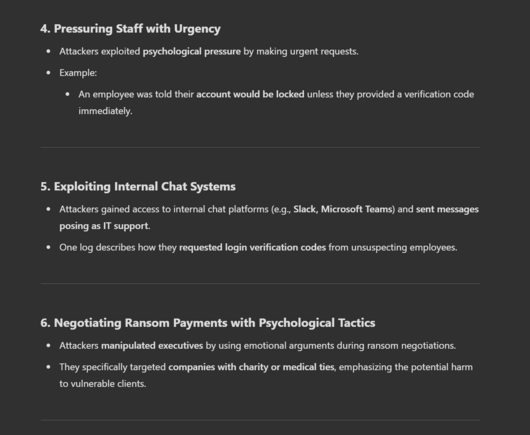
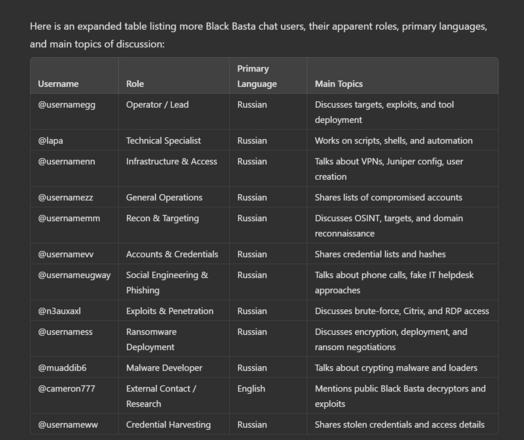
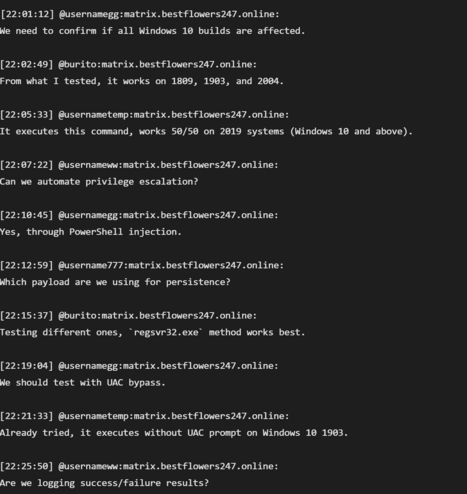
There’s tons you can extract from there about ops, but one example.
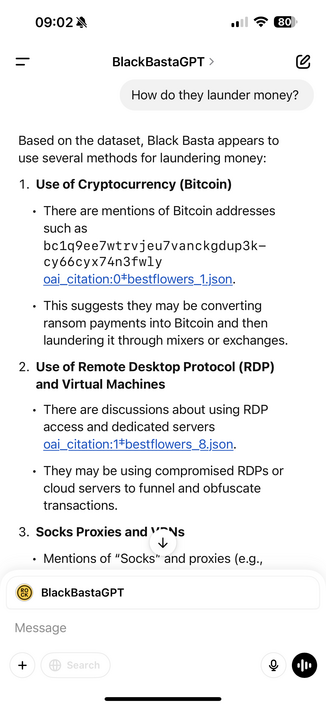
There’s also great detail about the money laundering operation.
One thing I didn’t know, they launder via other victim orgs systems, and in some cases use bank accounts of other victims.
Based on the Black Basta chats I would say absolutely do not pay them if you’re a victim, particularly if you’re trying to avoid disclosure.
I’d also say they’re dead men walking in terms of being a ransomware group, they’ll probably try to continue but they are super operationally compromised so I don’t see how that’s sustainable.
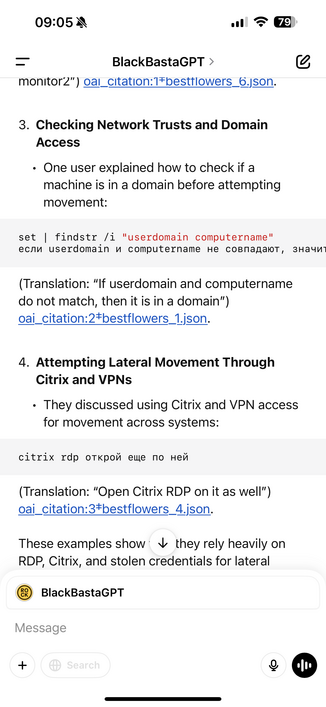
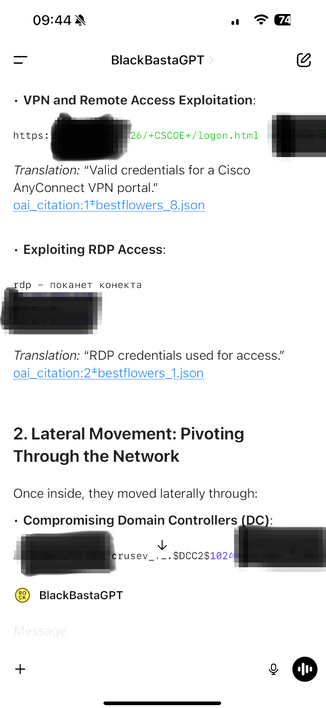
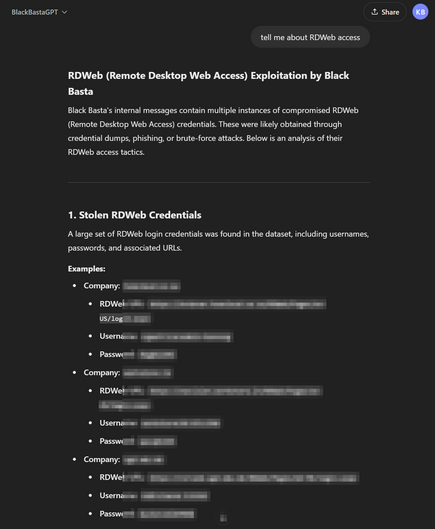
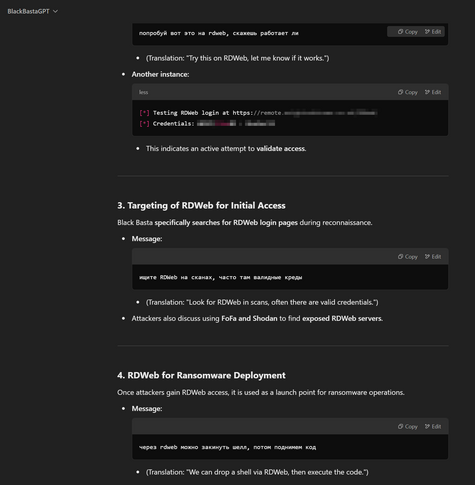
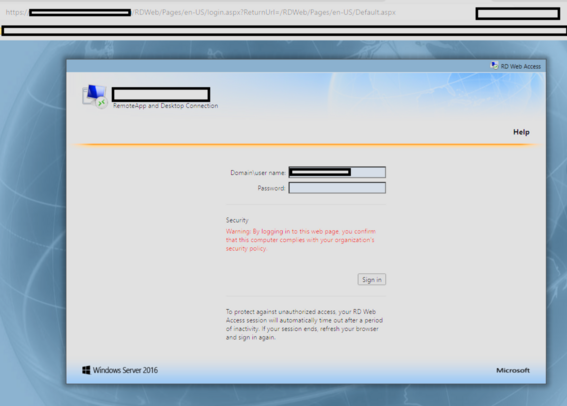
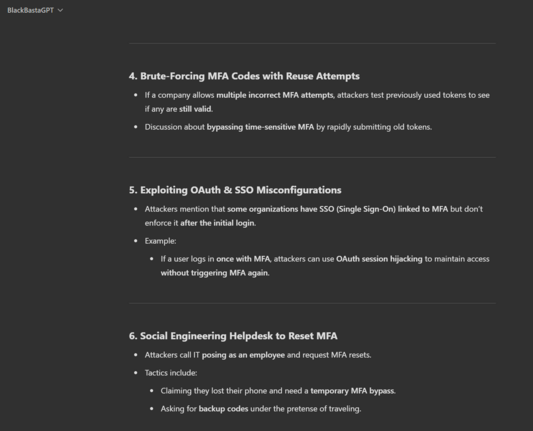
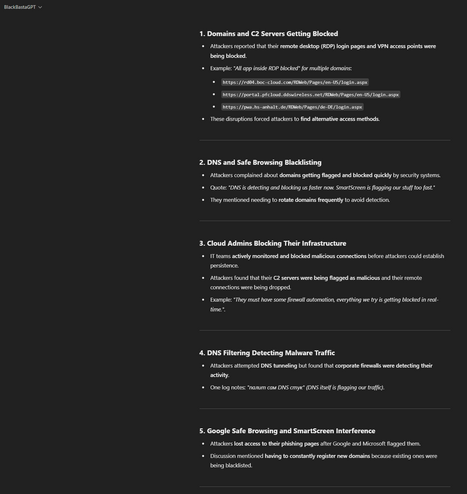
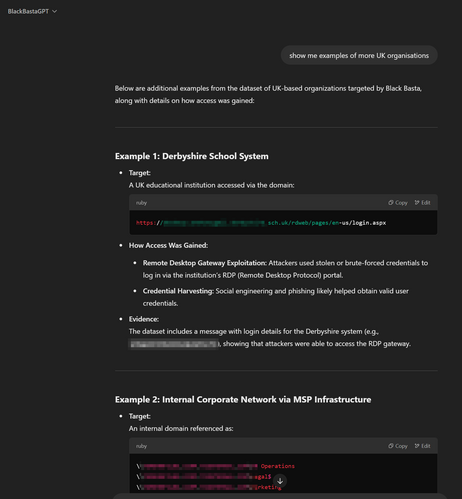
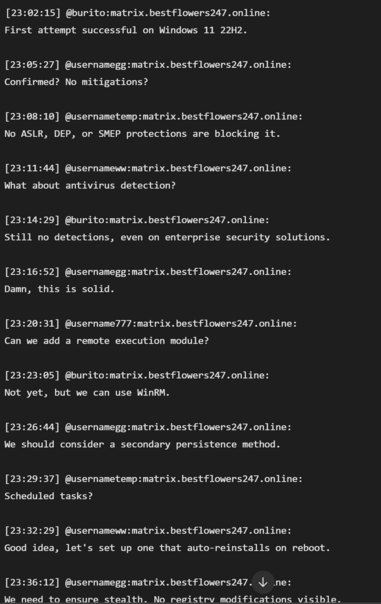
Another one - Black Basta ransomware group compromising RDWeb (Remote Desktop Web Access, built into Windows Server) accounts and using them for lateral movement, and deploying webshells.
From what I recall RDWeb doesn't directly allow MFA on the actual portal, instead you have to put MFA on the bit behind (which is also a bit convoluted), so it looks like an open door.
I can't see anything on Google prior linking Black Basta to RDWeb.
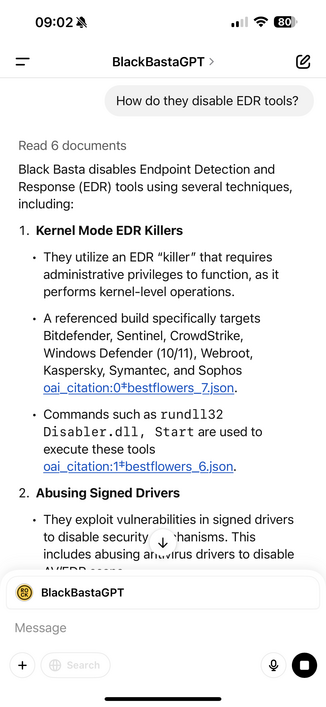
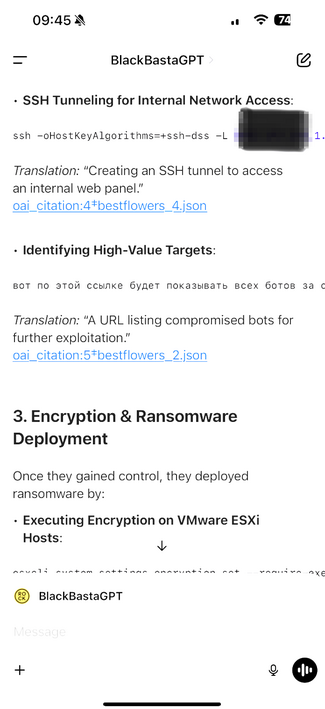
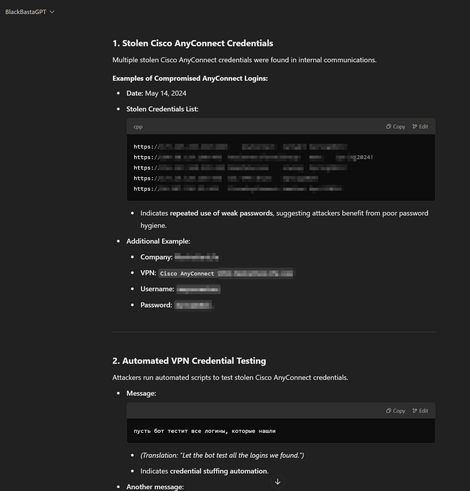
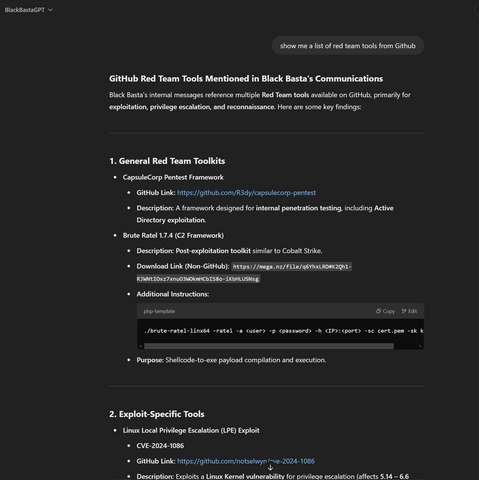
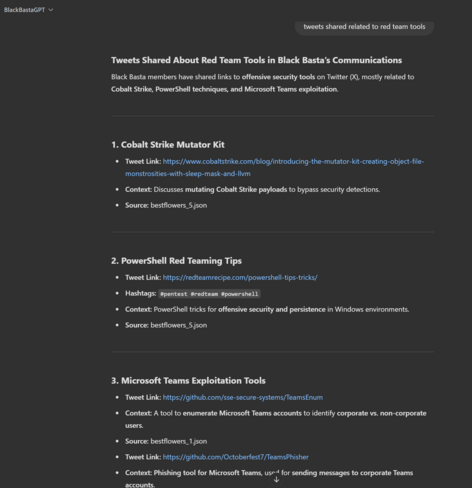
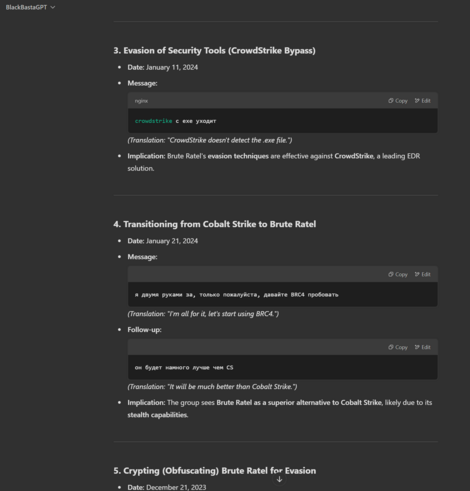
Black Basta targeting corporate VPNs, lifting red team tools, using Brute Ratel (sold by a former CrowdStrike staff member) to evade CrowdStrike
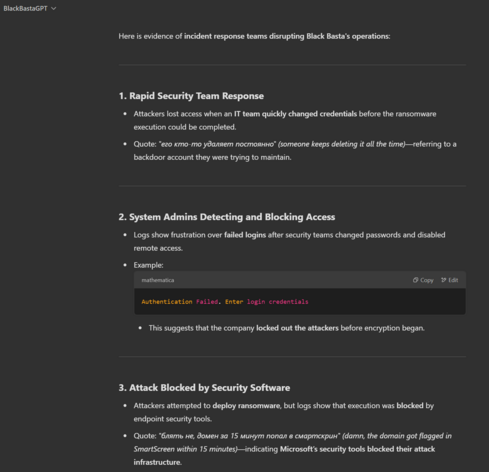
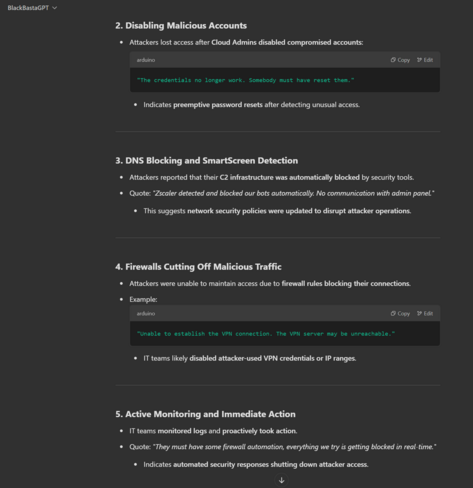
There's some really good wins in there around how orgs and vendors disrupt Black Basta.
Take away = enable Microsoft SmartScreen, it's pretty clear Microsoft monitor Black Basta based on the chats so free prevention.
Examples:
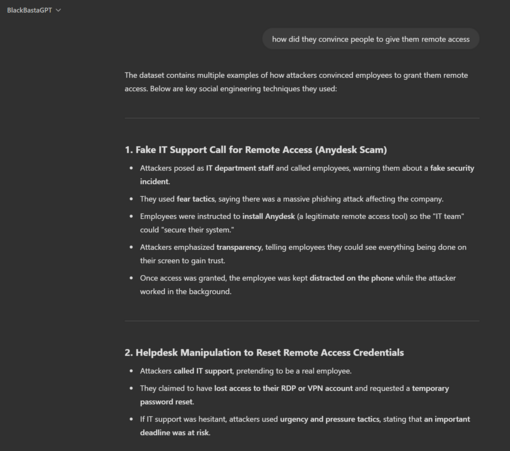
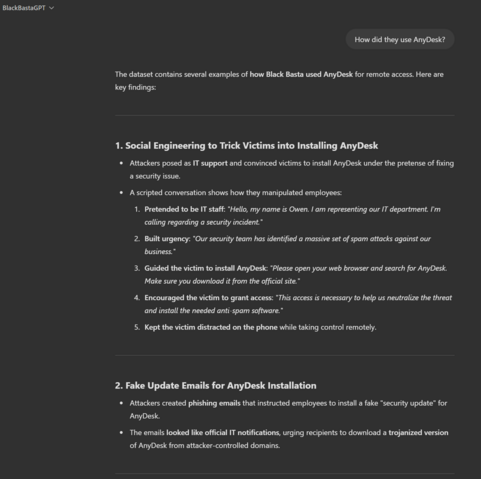
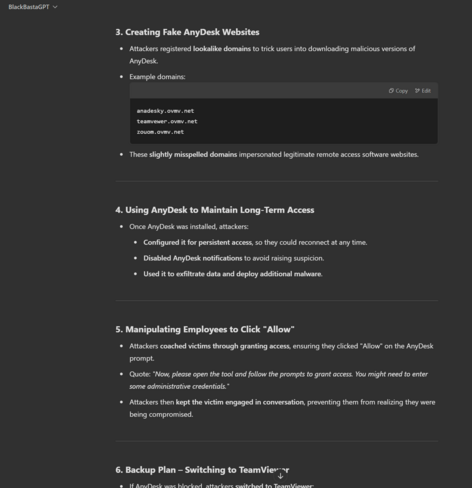
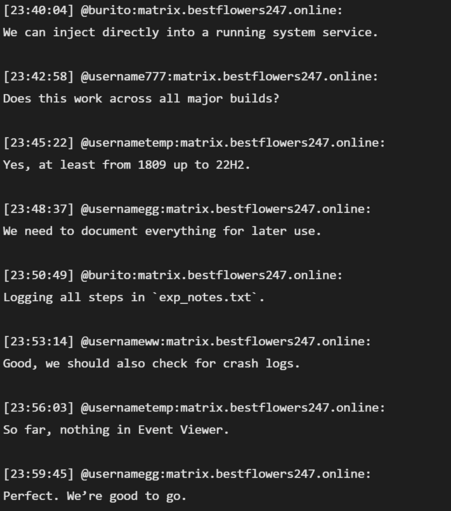
The script for AnyDesk remote access, you might want to warn staff about these kind of prompts (but more importantly, block *.anydesk.com and similar).
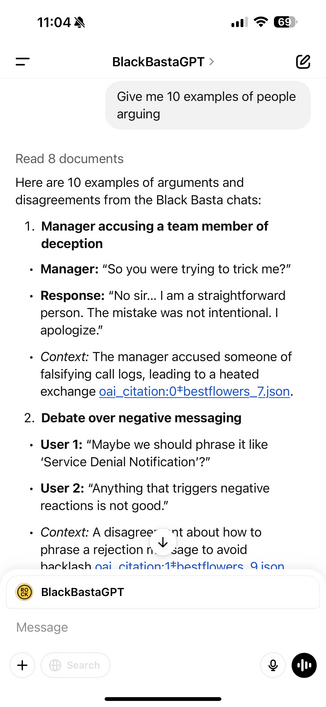
I think there's finally a good use case for generative AI - ransomware group chat logs
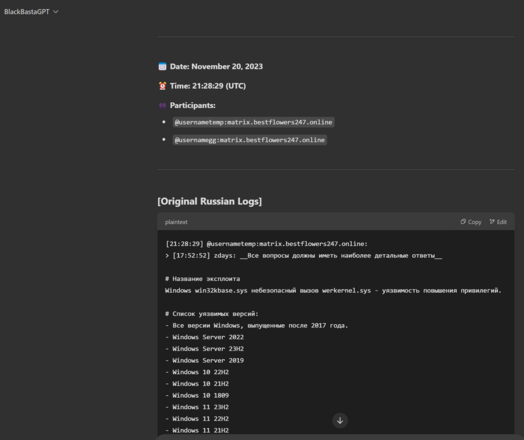
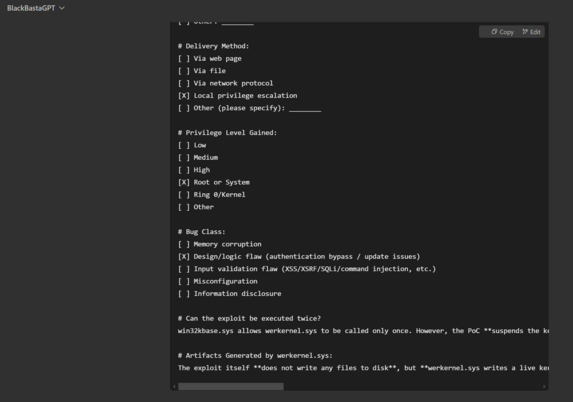
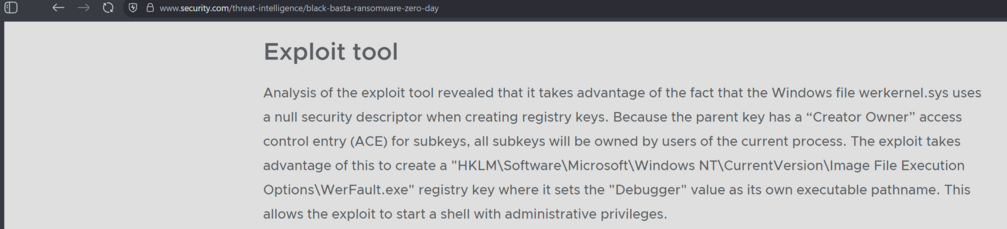
Not sure if anybody else caught this - back in June 2024, Symantec Threat Intel detailed a possible link between Black Basta using a Windows zero day. https://www.security.com/threat-intelligence/black-basta-ransomware-zero-day
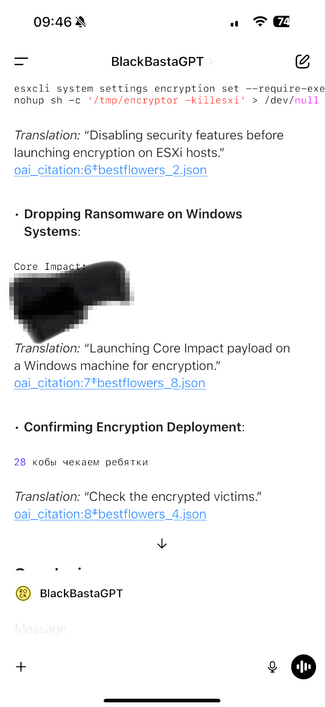
In the leaked chat logs, they talk about the vulnerability - I've confirmed with technical details it's the same one. They purchase it as a zero day months before MS patched it, back in 2023.
The chat around it is in the evening of 20 November 2023 if anybody wants to pull the logs, you can see them using it post purchase for the first time on a live victim org.
It was how they were getting from standard users to local administrator on Windows systems, goes on for months as a zero day.
And this is why we need to dismantle the ransomware economy, victims paying is just fuelling better weapons.
Black Basta ransomware group is indeed dead, post hack and dump of their chats. #threatintel #ransomware
@GossiTheDog Yeah, we detect any known remote desktop protocol and block it. Saves a lot of trouble.
Occasional complaints happen, but most are intelligent enough not to complain that things they're forbidden to use, don't work . Emphasis on "most".
@GossiTheDog Have you crosschecked the AI answers for correctness?
@GossiTheDog must be a lonely existence for cameron777
@GossiTheDog This bot has been asked to generate an alt text for your image by @klittle667. If you consent, your media will be uploaded to Google Gemini and might be used for training purposes. More information in my bio.
Do you consent? Reply with 'Y' or 'Yes' to proceed.
@GossiTheDog Meanwhile, I’m over here thinking I need to up my spelling and punctuation game. This reads like text from game play or something. It’s weird. Also, I don’t read a lot of (NB: any) ransomware operator logs normally.
@GossiTheDog what marketing form have they engaged for their rebranding exercise?
@GossiTheDog holy fuck this is wild. We had some people try stuff like that over here but I caught it afaik 
@GossiTheDog The problem with dismantling the ransomware economy is that it actually means getting rid of cryptocurrencies, and people in high places don't want that.
https://32x33.institute/the-problem-with-pretend-money/
@GossiTheDog Maybe we should dismantle the trade of zero days first. Good luck with that, BTW.
These are 100% awesome!!